Security News

A suspected China-nexus cyber espionage group has been attributed to an attacks targeting large business-to-business IT service providers in Southern Europe as part of a campaign codenamed...

A joint advisory issued by Australia, Canada, New Zealand, and the U.S. has warned of a broad cyber espionage campaign undertaken by People's Republic of China (PRC)-affiliated threat actors...
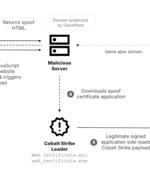
A China-linked nation-state group called TAG-112 compromised Tibetan media and university websites in a new cyber espionage campaign designed to facilitate the delivery of the Cobalt Strike...

U.S. telecoms giant T-Mobile has confirmed that it was also among the companies that were targeted by Chinese threat actors to gain access to valuable information. The adversaries, tracked as Salt...

After months of news reports that Chinese threat actors have breached the networks of US telecommunications and internet service providers, the FBI and the Cybersecurity and Infrastructure...

Feds don't name Salt Typhoon, but describe Beijing band's alleged deeds The US government has confirmed there was "a broad and significant cyber espionage campaign" conducted by China-linked...

Release the Kraken! China has accused unnamed foreign entities of using devices hidden in the seabed and bobbing on the waves to learn its maritime secrets.…

A suspected Russian hybrid espionage and influence operation has been observed delivering a mix of Windows and Android malware to target the Ukrainian military under the Telegram persona Civil...
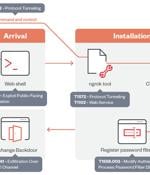
The Iranian threat actor known as OilRig has been observed exploiting a now-patched privilege escalation flaw impacting the Windows Kernel as part of a cyber espionage campaign targeting the...

Nation-state threat actors backed by Beijing broke into a "handful" of U.S. internet service providers (ISPs) as part of a cyber espionage campaign orchestrated to glean sensitive information, The...