Security News

Chinese spies are behind the data-stealing malware injected into Barracuda's Email Security Gateway devices globally as far back as October 2022, according to Mandiant. Mandiant, who has been working with Barracuda to investigate the exploit used and the malware subsequently deployed, today identified a China-based threat group it tracks as UNC4841, and said the snoops targeted a "Subset" of Barracuda ESG appliances across several regions and sectors.
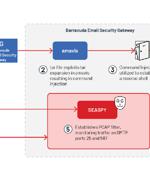
A suspected China-nexus threat actor dubbed UNC4841 has been linked to the exploitation of a recently patched zero-day flaw in Barracuda Email Security Gateway appliances since October 2022. "UNC4841 is an espionage actor behind this wide-ranging campaign in support of the People's Republic of China," Google-owned Mandiant said in a new report published today, describing the group as "Aggressive and skilled."

A report from the Microsoft Defender Experts reveals a new multi-staged adversary in the middle phishing attack combined with a business email compromise attack targeting banking and financial institutions. The phishing email impersonates one of the target's trusted vendors to appear more legitimate and blend with legitimate email traffic and bypass detections, especially when an organization has policies to automatically allow emails from trusted vendors.

Google says it has fixed a flaw that allowed a scammer to impersonate delivery service UPS on Gmail, after the data-hoarding web behemoth labeled the phony email as authentic. The problem stemmed from an issue in an email authentication program called Brand Indicators for Message Identification that aims to protect email users from brand spoofing and phishing attacks claiming to be from a trusted org.

You might imagine from the considerable number of email security tools on the market that the problem is being kept relatively in check, but you'd be wrong. Too many existing email security tools are based around analysis of historical attack data, so can only spot what they've seen before.

A critical remote command injection vulnerability in some Barracuda Network devices that the vendor patched 11 days ago has been exploited by miscreants - for at least the past seven months. Barracuda said it discovered the bug, tracked as CVE-2023-2868, in its Email Security Gateway appliance on May 19 and pushed a patch to all of these products globally the following day.

Enterprise security firm Barracuda on Tuesday disclosed that a recently patched zero-day flaw in its Email Security Gateway appliances had been abused by threat actors since October 2022 to backdoor the devices. The latest findings show that the critical vulnerability, tracked as CVE-2023-2868, has been actively exploited for at least seven months prior to its discovery.

The research shows that cybercriminals continue to barrage organizations with targeted email attacks, and many companies are struggling to keep up. While spear-phishing attacks are low-volume, they are widespread and highly successful compared to other types of email attacks.

Email protection and network security services provider Barracuda is warning users about a zero-day flaw that it said has been exploited to breach the company's Email Security Gateway appliances. "The vulnerability stems from incomplete input validation of a user-supplied.tar file as it pertains to the names of the files contained within the archive. As a consequence, a remote attacker can specifically format these file names in a particular manner that will result in remotely executing a system command through Perl's qx operator with the privileges of the Email Security Gateway product."

TechRepublic Premium Bring your own device policy PURPOSE The purpose of this Bring your own device policy from TechRepublic Premium is to provide requirements for BYOD usage and establish the steps that both users and the IT department should follow to initialize, support and remove devices from company access. These requirements must be followed as documented in order to protect company systems .....