Security News

Infosec in brief The July breach of Microsoft Exchange Online by suspected Chinese hackers is the next topic up for review by the Department of Homeland Security's Cyber Safety Review Board. The decision to investigate the July Outlook intrusion, and cloud security more broadly, was welcomed by senator Ron Wyden, who last week blamed Microsoft for its failure to protect cloud accounts belonging to US government officials and called for the CSRB to investigate the incident.

The Knight ransomware is being distributed in an ongoing spam campaign that pretends to be TripAdvisor complaints. Knight ransomware is a recent rebrand of the Cyclop Ransomware-as-a-Service, which switched its name at the end of July 2023.

The Department of Homeland Security's Cyber Safety Review Board has announced plans to conduct an in-depth review of cloud security practices following recent Chinese hacks of Microsoft Exchange accounts used by US government agencies. In mid-July 2023, Microsoft reported that a Chinese hacking group tracked as 'Storm-0558' breached the email accounts of 25 organizations, including US and Western European government agencies, using forged authentication tokens from a stolen Microsoft consumer signing key.

A sophisticated Facebook phishing campaign has been observed exploiting a zero-day flaw in Salesforce's email services, allowing threat actors to craft targeted phishing messages using the company's domain and infrastructure. What makes the attack notable is that the phishing kit is hosted as a game under the Facebook apps platform using the domain apps.

As a result of growing access to easy-to-use generative AI tools such as OpenAI's ChatGPT, malicious actors can now attempt more sophisticated attacks with alarming simplicity and regularity. Email continued to be the main vector for delivering malicious content, with as many as 1 in every 100 emails sent in the first half of 2023 found to be malicious.
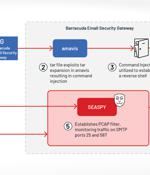
The U.S. Cybersecurity and Infrastructure Security Agency on Friday disclosed details of a "Novel persistent backdoor" called SUBMARINE deployed by threat actors in connection with the hack on Barracuda Email Security Gateway appliances. The findings come from an analysis of malware samples obtained from an unnamed organization that had been compromised by threat actors exploiting a critical flaw in ESG devices, CVE-2023-2868, which allows for remote command injection.

A stolen Microsoft security key may have allowed Beijing-backed spies to break into a lot more than just Outlook and Exchange Online email accounts. Microsoft still, to the best of our knowledge, does not know how this incredibly powerful private signing key was obtained, and has revoked that key.

Non-executable files containing malware were rarely shared, and could easily and automatically be identified if you tried to share one by mistake because they lacked the tell-tale starting bytes of a typical program file. Firstly, numerous malware families sneakily store at least some of their own needed data as added information in the personal part of such files, so that trying to bowdlerise, redact or rewrite the sensitive, "Unsharable" parts of the file causes the malware to stop working, or to behave differently.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.

Mil US military addresses were actually directed at. As a result of that one-character typo, medical data, identity documents, maps of military installations, travel itineraries, bookings for high-ranking military leaders, and more have been fired off at.