Security News
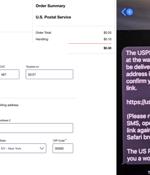
A new large-scale smishing campaign is targeting the U.S. by sending iMessages from compromised Apple iCloud accounts with an aim to conduct identity theft and financial fraud. "The Chinese-speaking threat actors behind this campaign are operating a package-tracking text scam sent via iMessage to collect personally identifying information and payment credentials from victims, in the furtherance of identity theft and credit card fraud," Resecurity said in an analysis published last week.

Adversary-sponsored research contests on cybercriminal forums focus on new methods of attack and evasion, according to Sophos. The contests mirror legitimate security conference 'Call For Papers' and provide the winners considerable financial rewards and recognition from peers and also potential jobs.
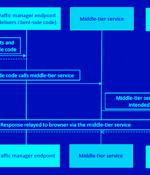
Cybersecurity researchers have discovered a case of privilege escalation associated with a Microsoft Entra ID application by taking advantage of an abandoned reply URL. "An attacker could leverage this abandoned URL to redirect authorization codes to themselves, exchanging the ill-gotten authorization codes for access tokens," Secureworks Counter Threat Unit said in a technical report published last week. Reply URL, also called redirect URI, refers to the location where the authorization server sends the user once the app has been successfully authorized and granted an authorization code or access token.

Cybercriminals employ artificial intelligence to create complex email threats like phishing and business email compromise attacks, while modern email security systems use AI to counter these attacks, according to Perception Point and Osterman Research. Cybercriminals have shown rapid adoption of AI tools to their favor with 91.1% of organizations reporting that they have already encountered email attacks that have been enhanced by AI, and 84.3% expecting that AI will continue to be utilized to circumvent existing security systems.

An international law enforcement operation led by Interpol has led to the arrest of 14 suspected cybercriminals in an operation codenamed 'Africa Cyber Surge II,' launched in April 2023. Interpol has been actively fighting cybercrime in recent months, disrupting multi-million operations and seizing widely-used crime platforms.

A coordinated law enforcement operation across 25 African countries has led to the arrest of 14 suspected cybercriminals, INTERPOL announced Friday. "The four-month Africa Cyber Surge II operation was launched in April 2023 and focused on identifying cybercriminals and compromised infrastructure," the agency said.

Threat actors' use of Cloudflare R2 to host phishing pages has witnessed a 61-fold increase over the past six months. "The majority of the phishing campaigns target Microsoft login credentials, although there are some pages targeting Adobe, Dropbox, and other cloud apps," Netskope security researcher Jan Michael said.
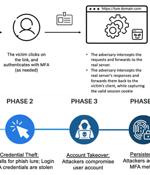
Threat actors are increasingly using a phishing-as-a-service toolkit dubbed EvilProxy to pull off account takeover attacks aimed at high-ranking executives at prominent companies. According to Proofpoint, an ongoing hybrid campaign has leveraged the service to target thousands of Microsoft 365 user accounts, sending approximately 120,000 phishing emails to hundreds of organizations worldwide between March and June 2023.

Services offered by an obscure Iranian company known as Cloudzy are being leveraged by multiple threat actors, including cybercrime groups and nation-state crews. The Texas-based cybersecurity firm said the company acts as a command-and-control provider, which provides attackers with Remote Desktop Protocol virtual private servers and other anonymized services that ransomware affiliates and others use to pull off the cybercriminal endeavors.

In the wake of WormGPT, a ChatGPT clone trained on malware-focused data, a new generative artificial intelligence hacking tool called FraudGPT has emerged, and at least another one is under development that is allegedly based on Google's AI experiment, Bard. Both AI-powered bots are the work of the same individual, who appears to be deep in the game of providing chatbots trained specifically for malicious purposes ranging from phishing and social engineering, to exploiting vulnerabilities and creating malware.