Security News

The U.S. Cybersecurity and Infrastructure Security Agency this week released an Industrial Control Systems advisory warning of multiple vulnerabilities in Mitsubishi Electric GX Works3 engineering software. "Successful exploitation of these vulnerabilities could allow unauthorized users to gain access to the MELSEC iQ-R/F/L series CPU modules and the MELSEC iQ-R series OPC UA server module or to view and execute programs," the agency said.
A critical security vulnerability has been disclosed in the Quarkus Java framework that could be potentially exploited to achieve remote code execution on affected systems. "The vulnerability is found in the Dev UI Config Editor, which is vulnerable to drive-by localhost attacks that could lead to remote-code execution," Contrast Security researcher Joseph Beeton, who reported the bug, said in a write-up.
A critical security vulnerability has been disclosed in the Quarkus Java framework that could be potentially exploited to achieve remote code execution on affected systems. "The vulnerability is found in the Dev UI Config Editor, which is vulnerable to drive-by localhost attacks that could lead to remote-code execution," Contrast Security researcher Joseph Beeton, who reported the bug, said in a write-up.

Three Android applications that allow users to use devices as remote keyboards for their computers have critical vulnerabilities that could expose key presses and enable remote code execution. CVE-2022-45479 - PC Keyboard flow allowing a remote unauthenticated user to send instructions to the server to execute arbitrary code without requiring authorization or authentication.

The U.S. Cybersecurity and Infrastructure Security Agency on Monday added a critical flaw impacting Oracle Fusion Middleware to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation. The vulnerability, tracked as CVE-2021-35587, carries a CVSS score of 9.8 and impacts Oracle Access Manager versions 11.1.2.3.0, 12.2.1.3.0, and 12.2.1.4.0.

The U.S. Cybersecurity and Infrastructure Security Agency on Monday added a critical flaw impacting Oracle Fusion Middleware to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation. The vulnerability, tracked as CVE-2021-35587, carries a CVSS score of 9.8 and impacts Oracle Access Manager versions 11.1.2.3.0, 12.2.1.3.0, and 12.2.1.4.0.
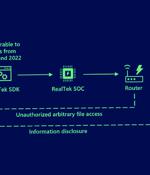
Microsoft said its own investigation into the attack activity uncovered Boa as a common link, assessing that the intrusions were directed against exposed IoT devices running the web server. "Despite being discontinued in 2005, the Boa web server continues to be implemented by different vendors across a variety of IoT devices and popular software development kits," the company said.

Australian software company Atlassian has rolled out security updates to address two critical flaws affecting Bitbucket Server, Data Center, and Crowd products. CVE-2022-43781, which Atlassian said was introduced in version 7.0.0 of Bitbucket Server and Data Center, affects versions 7.0 to 7.21 and 8.0 to 8.4.

Atlassian has released updates to address critical-severity updates in its centralized identity management platform, Crowd Server and Data Center, and in Bitbucket Server and Data Center, the company's solution for Git repository management. Rated critical, the issue in Crowd Server and Data Center is tracked as CVE-2022-43782 and is a misconfiguration that allows an attacker to bypass password checks when authenticating as the Crowd app and to call privileged API endpoints.

Spotify's Backstage has been discovered as vulnerable to a severe security flaw that could be exploited to gain remote code execution by leveraging a recently disclosed bug in a third-party module. The vulnerability, at its core, takes advantage of a critical sandbox escape in vm2, a popular JavaScript sandbox library, that came to light last month.