Security News

Cisco and VMware have released security updates to address critical security flaws in their products that could be exploited by malicious actors to execute arbitrary code on affected systems. The most severe of the vulnerabilities is a command injection flaw in Cisco Industrial Network Director, which resides in the web UI component and arises as a result of improper input validation when uploading a Device Pack.
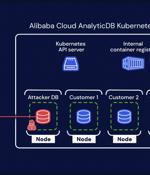
A chain of two critical flaws has been disclosed in Alibaba Cloud's ApsaraDB RDS for PostgreSQL and AnalyticDB for PostgreSQL that could be exploited to breach tenant isolation protections and access sensitive data belonging to other customers. "The vulnerabilities potentially allowed unauthorized access to Alibaba Cloud customers' PostgreSQL databases and the ability to perform a supply chain attack on both Alibaba database services, leading to an RCE on Alibaba database services," cloud security firm Wiz said in a new report shared with The Hacker News.

Print management software developer PaperCut is warning customers to update their software immediately, as hackers are actively exploiting flaws to gain access to vulnerable servers. Today, the software developer updated its March 2023 security bulletin to warn customers that the vulnerabilities are now actively exploited by hackers.

A fresh round of patches has been made available for the vm2 JavaScript library to address two critical flaws that could be exploited to break out of the sandbox protections. Both the flaws - CVE-2023-29199 and CVE-2023-30547 - are rated 9.8 out of 10 on the CVSS scoring system and have been addressed in versions 3.9.16 and 3.9.17, respectively.

Security researchers and experts warn of a critical vulnerability in the Windows Message Queuing middleware service patched by Microsoft during this month's Patch Tuesday and exposing hundreds of thousands of systems to attacks. MSMQ is available on all Windows operating systems as an optional component that provides apps with network communication capabilities with "Guaranteed message delivery," and it can be enabled via PowerShell or the Control Panel.

Enterprise software vendor SAP has released its April 2023 security updates for several of its products, which includes fixes for two critical-severity vulnerabilities that impact the SAP Diagnostics Agent and the SAP BusinessObjects Business Intelligence Platform. In total, SAP has released 24 notes, 19 of which concern new issues of varying importance, and five are updates to previous bulletins.

The maintainers of the vm2 JavaScript sandbox module have shipped a patch to address a critical flaw that could be abused to break out of security boundaries and execute arbitrary shellcode. The flaw, which affects all versions, including and prior to 3.9.14, was reported by researchers from South Korea-based KAIST WSP Lab on April 6, 2023, prompting vm2 to release a fix with version 3.9.15 on Friday.

Proof-of-concept exploit code has been released for a recently disclosed critical vulnerability in the popular VM2 library, a JavaScript sandbox that is used by multiple software to run code securely in a virtualized environment. The researchers who found that the VM2 library handled improperly the host objects passed to the 'Error.

The U.S. Cybersecurity and Infrastructure Security Agency has published eight Industrial Control Systems advisories warning of critical flaws affecting products from Hitachi Energy, mySCADA Technologies, Industrial Control Links, and Nexx. Topping the list is CVE-2022-3682, impacting Hitachi Energy's MicroSCADA System Data Manager SDM600 that could allow an attacker to take remote control of the product.

According to Etay Maor, Senior Director Security Strategy at Cato Networks, "It's interesting to note critical infrastructure doesn't necessarily have to be power plants or electricity. A nation's monetary system or even a global monetary system can be and should be considered a critical infrastructure as well." Not to mention the infamous Colonial Pipeline attack, which has become the poster child of critical infrastructure attacks.