Security News

The U.S. Cybersecurity and Infrastructure Security Agency warned today of a critical remote code execution flaw in the Ruckus Wireless Admin panel actively exploited by a recently discovered DDoS botnet. While this security bug was addressed in early February, many owners are likely yet to patch their Wi-Fi access points.

U.S. cybersecurity and intelligence agencies have warned of attacks carried out by a threat actor known as the Bl00dy Ransomware Gang that attempt to exploit vulnerable PaperCut servers against the education facilities sector in the country. "The Bl00dy Ransomware Gang gained access to victim networks across the Education Facilities Subsector where PaperCut servers vulnerable to CVE-2023-27350 were exposed to the internet," the agencies said.
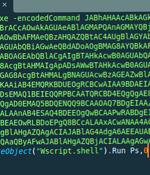
A previously undetected advanced persistent threat actor dubbed Red Stinger has been linked to attacks targeting Eastern Europe since 2020. Red Stinger overlaps with a threat cluster Kaspersky revealed under the name Bad Magic last month as having targeted government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea last year.

A nascent botnet called Andoryu has been found to exploit a now-patched critical security flaw in the Ruckus Wireless Admin panel to break into vulnerable devices. While the malware is known to weaponize remote code execution flaws in GitLab and Lilin DVR for propagation, the addition of CVE-2023-25717 shows that Andoryu is actively expanding its exploit arsenal to ensnare more devices into the botnet.

A new malware botnet named 'AndoryuBot' is targeting a critical-severity flaw in the Ruckus Wireless Admin panel to infect unpatched Wi-Fi access points for use in DDoS attacks.Tracked as CVE-2023-25717, the flaw impacts all Ruckus Wireless Admin panels version 10.4 and older, allowing remote attackers to perform code execution by sending unauthenticated HTTP GET requests to vulnerable devices.
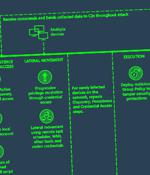
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut print management software, Microsoft said. The tech giant's threat intelligence team said it observed both Mango Sandstorm and Mint Sandstorm weaponizing CVE-2023-27350 in their operations to achieve initial access.

Cisco has revealed the existence of a critical vulnerability in the web-based management interface of Cisco SPA112 2-Port Phone Adapters. "This vulnerability is due to a missing authentication process within the firmware upgrade function. An attacker could exploit this vulnerability by upgrading an affected device to a crafted version of firmware," Cisco's security advisory explains.

The U.S. Cybersecurity and Infrastructure Security Agency on Tuesday released an Industrial Control Systems advisory about a critical flaw affecting ME RTU remote terminal units. The security vulnerability, tracked as CVE-2023-2131, has received the highest severity rating of 10.0 on the CVSS scoring system for its low attack complexity.

Threats - from cybersecurity exploits to climate change - have major implications for those systems, and with emerging technologies only increasing demand for power and creating new vulnerabilities, maintaining infrastructure is as much about resiliency as keeping the juice flowing, the air conditioners running and the security cameras pointed at the door. Joseph Vijay, CEO of Intelli-Systems, a Melbourne, Australia-based critical systems infrastructure company that supports infrastructure for mines, hospitals, data centers and more, said buyers of critical infrastructure need to focus more on how the infrastructure purchase decisions they make will influence both their bottom line and the environment.

Overcoming industry obstacles for decentralized digital identitiesIn this Help Net Security interview, Eve Maler, CTO at ForgeRock, talks about how digital identities continue to play a critical role in how we access online services securely. PaperCut vulnerabilities leveraged by Clop, LockBit ransomware affiliatesClop and LockBit ransomware affiliates are behind the recent attacks exploiting vulnerabilities in PaperCut application servers, according to Microsoft and Trend Micro researchers.