Security News

MOVEit Transfer zero-day attacks: The latest infoProgress Software has updated the security advisory and confirmed that the vulnerability is a SQL injection vulnerability in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain unauthorized access to MOVEit Transfer's database. Kali Linux 2023.2 released: New tools, a pre-built Hyper-V image, a new audio stack, and more!Offensive Security has released Kali Linux 2023.2, the latest version of its popular penetration testing and digital forensics platform.

A critical zero-day vulnerability in Progress Software's enterprise managed file transfer solution MOVEit Transfer is being exploited by attackers to grab corporate data. " could lead to escalated privileges and potential unauthorized access to the environment," the company warned on Wednesday, and advised customers to take action to protect their MOVEit Transfer environment, "While our team produces a patch."

WordPress has issued an automatic update to address a critical flaw in the Jetpack plugin that's installed on over five million sites.The vulnerability, which was unearthed during an internal security audit, resides in an API present in the plugin since version 2.0, which was released in November 2012.

Hackers are performing widespread exploitation of a critical-severity command injection flaw in Zyxel networking devices, tracked as CVE-2023-28771, to install malware. The flaw, which is present in the default configuration of impacted firewall and VPN devices, can be exploited to perform unauthenticated remote code execution using a specially crafted IKEv2 packet to UDP port 500 on the device.

Everyone is writing about an interagency and international report on Chinese hacking of US critical infrastructure. Lots of interesting details about how the group, called Volt Typhoon, accesses target networks and evades detection.

Cybersecurity researchers have found "Backdoor-like behavior" within Gigabyte systems, which they say enables the UEFI firmware of the devices to drop a Windows executable and retrieve updates in an unsecure format. "Most Gigabyte firmware includes a Windows Native Binary executable embedded inside of the UEFI firmware," John Loucaides, senior vice president of strategy at Eclypsium, told The Hacker News.
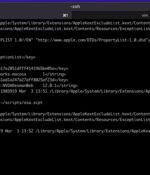
Microsoft has shared details of a now-patched flaw in Apple macOS that could be abused by threat actors with root access to bypass security enforcements and perform arbitrary actions on affected devices. "The most straight-forward implication of a SIP bypass is that an attacker can create files that are protected by SIP and therefore undeletable by ordinary means," Microsoft researchers Jonathan Bar Or, Michael Pearse, and Anurag Bohra said.

How to do that efficiently and effectively is no small task - but with a small investment of time, you can master threat hunting and save your organization millions of dollars. This article offers a detailed explanation of threat hunting - what it is, how to do it thoroughly and effectively, and how cyber threat intelligence can bolster your threat-hunting efforts.

Automattic, the company behind the open-source WordPress content management system, has started force installing a security patch on millions of websites today to address a critical vulnerability in the Jetpack WordPress plug-in. According to the official WordPress plug-in repository, the plug-in is maintained by Automattic, and it now has over 5 million active installations.

Multiple security flaws uncovered in Sonos One wireless speakers could be potentially exploited to achieve information disclosure and remote code execution, the Zero Day Initiative said in a report published last week. The list of four flaws, which impact Sonos One Speaker 70.3-35220, is below -.