Security News
Nearly 2,000 Citrix NetScaler instances have been compromised with a backdoor by weaponizing a recently disclosed critical security vulnerability as part of a large-scale attack. CVE-2023-3519 refers to a critical code injection vulnerability impacting NetScaler ADC and Gateway servers that could lead to unauthenticated remote code execution.

Two stack-based buffer overflows collectively tracked as CVE-2023-32560 impact Ivanti Avalanche, an enterprise mobility management solution designed to manage, monitor, and secure a wide range of mobile devices. The flaws are rated critical and are remotely exploitable without user authentication, potentially allowing attackers to execute arbitrary code on the target system.
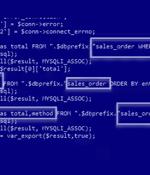
E-commerce sites using Adobe's Magento 2 software are the target of an ongoing campaign that has been active since at least January 2023. The attacks, dubbed Xurum by Akamai, leverage a now-patched critical security flaw in Adobe Commerce and Magento Open Source that, if successfully exploited, could lead to arbitrary code execution.

Ecommerce stores using Adobe's open source Magento 2 software are being targeted by an ongoing exploitation campaign based on a critical vulnerability that was patched last year, on February 13, 2022. "The attacker seems to be interested in payment stats from the orders in the victim's Magento store placed in the past 10 days," they said.

August 2023 Patch Tuesday is here; among the 76 CVE-numbered issues fixed by Microsoft this time around is a DoS vulnerability in. There is a Microsoft Office "Defense in Depth Update" available that, according to Microsoft, stops the attack chain leading to CVE-2023-36884, a Windows Search RCE vulnerability that has been previously exploited by Russian hackers in targeted attacks.
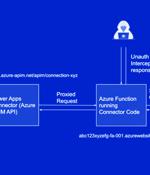
Microsoft on Friday disclosed that it has addressed a critical security flaw impacting Power Platform, but not before it came under criticism for its failure to swiftly act on it. "The vulnerability could lead to unauthorized access to Custom Code functions used for Power Platform custom connectors," the tech giant said.

PaperCut recently fixed a critical security vulnerability in its NG/MF print management software that allows unauthenticated attackers to gain remote code execution on unpatched Windows servers. While it only impacts servers in non-default configurations where the external device integration setting is toggled, Horizon3 said in a report published on Friday that most Windows PaperCut servers have it enabled.

Cybersecurity researchers have discovered a bypass for a recently fixed actively exploited vulnerability in some versions of Ivanti Endpoint Manager Mobile, prompting Ivanti to urge users to update to the latest version of the software. Tracked as CVE-2023-35082 and discovered by Rapid7, the issue "Allows unauthenticated attackers to access the API in older unsupported versions of MobileIron Core.".

IT software company Ivanti disclosed today a new critical security vulnerability in its MobileIron Core mobile device management software. "MobileIron Core 11.2 has been out of support since March 15, 2022. Therefore, Ivanti will not be issuing a patch or any other remediations to address this vulnerability in 11.2 or earlier versions. Upgrading to the latest version of Ivanti Endpoint Manager Mobile is the best way to protect your environment from threats," the company said.

A critical security flaw in Ivanti's mobile endpoint management code was exploited and used to compromise 12 Norwegian government agencies before the vendor plugged the hole. On Monday, the US government's Cybersecurity and Infrastructure Security Agency added CVE-2023-35078 to its Known Exploited Vulnerabilities Catalog that should be urgently patched.