Security News

Active Directory (AD), Microsoft’s on-premises directory service for Windows domain networks, is so widely used for enterprise identity and access management that compromising it has become almost...

Until just a couple of years ago, only a handful of IAM pros knew what service accounts are. In the last years, these silent Non-Human-Identities (NHI) accounts have become one of the most...

Cybersecurity researchers have uncovered a never-before-seen botnet comprising an army of small office/home office (SOHO) and IoT devices that are likely operated by a Chinese nation-state threat...
Roblox developers are the target of a persistent campaign that seeks to compromise systems through bogus npm packages, once again underscoring how threat actors continue to exploit the trust in...

Advanced, persistent attackers have exploited a zero-day vulnerability (CVE-2024-39717) in Versa Director to compromise US-based managed service providers with a custom-made web shell dubbed...

As cloud infrastructure becomes the backbone of modern enterprises, ensuring the security of these environments is paramount. With AWS (Amazon Web Services) still being the dominant cloud it is...

Unicoin said it regained access to its G-Suite on August 13, and it's still working to determine to what extent company data has been compromised. Attackers definitely broke into the company G-Suite.

New research from cybersecurity company Volexity revealed details about a highly sophisticated attack deployed by a Chinese-speaking cyberespionage threat actor named StormBamboo. StormBamboo compromised an ISP to modify some DNS answers to queries from systems requesting legitimate software updates.

Two cross-site scripting vulnerabilities affecting Roundcube could be exploited by attackers to steal users' emails and contacts, email password, and send emails from their account. "No user interaction beyond viewing the attacker's email is required to exploit. For CVE-2024-42008, a single click by the victim is needed for the exploit to work, but the attacker can make this interaction unobvious for the user," Sonar vulnerability researcher Oskar Zeino-Mahmalat noted.
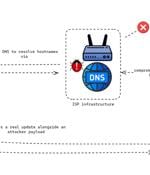
The China-linked threat actor known as Evasive Panda compromised an unnamed internet service provider to push malicious software updates to target companies in mid-2023, highlighting a new level of sophistication associated with the group. It was also found to have targeted an international non-governmental organization in Mainland China with MgBot delivered via update channels of legitimate applications like Tencent QQ. While it was speculated that the trojanized updates were either the result of a supply chain compromise of Tencent QQ's update servers or a case of an adversary-in-the-middle attack, Volexity's analysis confirms it's the latter stemming from a DNS poisoning attack at the ISP level.