Security News

Get best practice advice on how to safeguard your cloud infrastructure from SANS Sponsored Post According to the 2024 IBM Cost of the Data Breach Report 40 percent of data breaches identified...

As the era of quantum computing draws closer, businesses face a new and unprecedented threat to data security: “Q-day.” This looming turning point—when quantum machines can break traditional...

Datadog advises Australian and APAC companies to phase out long-lived cloud credentials.

Are you using the cloud or thinking about transitioning? Undoubtedly, multi-cloud and hybrid environments offer numerous benefits for organizations. However, the cloud's flexibility, scalability,...

Tap into the infinite scalability... of pricing Re:Invent Amazon Web Services has a new incident response service that combines automation and people to protect customers' AWS accounts - at a hefty price.…

Microsoft has addressed four security flaws impacting its artificial intelligence (AI), cloud, enterprise resource planning, and Partner Center offerings, including one that it said has been...
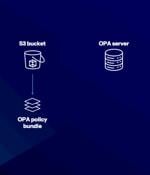
Cybersecurity researchers have disclosed two new attack techniques against infrastructure-as-code (IaC) and policy-as-code (PaC) tools like HashiCorp's Terraform and Open Policy Agent (OPA) that...

In this Help Net Security interview, Brooke Motta, CEO of RAD Security, talks about how cloud-specific threats have evolved and what companies should be watching out for. She discusses the growing...
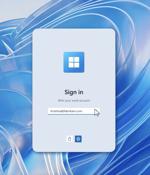
Microsoft unveiled Windows 365 Link, their first purpose-built Cloud PC device for instant, secure connection to Windows 365. Sign-in screen with USB security key option (Source: Microsoft)...

Google Cloud unveiled its Cybersecurity Forecast for 2025, offering a detailed analysis of the emerging threat landscape and key security trends that organizations worldwide should prepare for....