Security News

Incident response today is too time consuming and manual, leaving organizations vulnerable to damage due to their inability to efficiently investigate and respond to identified threats, according...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads. "The VBScript and PowerShell...

Tenable researchers have discovered a critical vulnerability (CVE-2024-4323) in Fluent Bit, a logging utility used by major cloud providers and tech companies, which may be leveraged for denial of...

Current demand for cloud security specialists far exceeds available talent. Especially for companies seeking protection in multicloud environments, professionals with vendor-neutral knowledge and...

A critical Fluent Bit vulnerability that can be exploited in denial-of-service and remote code execution attacks impacts all major cloud providers and many technology giants. Fluent Bit is an extremely popular logging and metrics solution for Windows, Linux, and macOS embedded in major Kubernetes distributions, including those from Amazon AWS, Google GCP, and Microsoft Azure.

Cloud security incidents are alarmingly on the rise, with 61% of organizations reporting breaches within the last year, marking a significant increase from 24% the year before, according to Check...
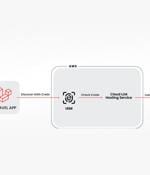
Cybersecurity researchers have discovered a novel attack that employs stolen cloud credentials to target cloud-hosted large language model (LLM) services with the goal of selling access to other...
You might not have knowledge of cloud security best practices, in-house expertise, or the desire to spend significant resources towards cloud security management. The CIS Controls consist of prescriptive, prioritized, and simplified security best practices that you can use to strengthen your cybersecurity posture across your environments, including in the cloud.

״Defenders think in lists, attackers think in graphs,” said John Lambert from Microsoft, distilling the fundamental difference in mindset between those who defend IT systems and those who try to...