Security News
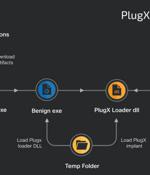
The China-based threat actor known as Mustang Panda has been observed refining and retooling its tactics and malware to strike entities located in Asia, the European Union, Russia, and the U.S. "Mustang Panda is a highly motivated APT group relying primarily on the use of topical lures and social engineering to trick victims into infecting themselves," Cisco Talos said in a new report detailing the group's evolving modus operandi. The group is known to have targeted a wide range of organizations since at least 2012, with the actor primarily relying on email-based social engineering to gain initial access to drop PlugX, a backdoor predominantly deployed for long-term access.

Dubbed "Operation CuckooBees" by Israeli cybersecurity company Cybereason, the massive intellectual property theft operation enabled the threat actor to exfiltrate hundreds of gigabytes of information. "The attackers targeted intellectual property developed by the victims, including sensitive documents, blueprints, diagrams, formulas, and manufacturing-related proprietary data," the researchers said.
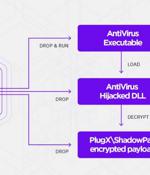
A Chinese-aligned cyberespionage group has been observed striking the telecommunication sector in Central Asia with versions of malware such as ShadowPad and PlugX. Cybersecurity firm SentinelOne tied the intrusions to an actor it tracks under the name "Moshen Dragon," with tactical overlaps between the collective and another threat group referred to as Nomad Panda. ShadowPad, labeled a "Masterpiece of privately sold malware in Chinese espionage," emerged as a successor to PlugX in 2015, even as variants of the latter have continually popped up as part of different campaigns associated with Chinese threat actors.

A Chinese state-sponsored espionage group known as Override Panda has resurfaced in recent weeks with a new phishing attack with the goal of stealing sensitive information. "The Chinese APT used a spear-phishing email to deliver a beacon of a Red Team framework known as 'Viper,'" Cluster25 said in a report published last week.

A China-linked government-sponsored threat actor has been observed targeting Russian speakers with an updated version of a remote access trojan called PlugX. Secureworks attributed the attempted intrusions to a threat actor it tracks as Bronze President, and by the wider cybersecurity community under the monikers Mustang Panda, TA416, HoneyMyte, RedDelta, and PKPLUG. "The war in Ukraine has prompted many countries to deploy their cyber capabilities to gain insight about global events, political machinations, and motivations," the cybersecurity firm said in a report shared with The Hacker News. Chief among its tools is PlugX, a Windows backdoor that enables threat actors to execute a variety of commands on infected systems and which has been employed by several Chinese state-sponsored actors over the years.

Security researchers analyzing a phishing campaign targeting Russian officials found evidence that points to the China-based threat actor tracked as Mustang Panda. The threat group was previously seen orchestrating intelligence collection campaigns against European targets, employing phishing lures inspired by the Russian invasion of Ukraine.

In a first for a major Chinese tech company, drone-maker DJI Technologies announced on Tuesday that it will temporarily suspend business in both Russia and Ukraine. "DJI is internally reassessing compliance requirements in various jurisdictions. Pending the current review, DJI will temporarily suspend all business activities in Russia and Ukraine. We are engaging with customers, partners and other stakeholders regarding the temporary suspension of business operations in the affected territories," declared DJI in a canned statement.

Threat analysts report that zero-day vulnerability exploitation is on the rise, with Chinese hackers using most of them in attacks last year. Zero-day disclosures are of particular interest to hackers because they have a wider exploitation window until vendors address the flaws and clients start applying the updates.

The Chinese-backed Hafnium hacking group has been linked to a piece of a new malware that's used to maintain persistence on compromised Windows environments. Microsoft Threat Intelligence Center, which dubbed the defense evasion malware "Tarrask," characterized it as a tool that creates "Hidden" scheduled tasks on the system.

China-linked adversaries have been attributed to an ongoing onslaught against Indian power grid organizations, one year after a concerted campaign targeting critical infrastructure in the country came to light. Most of the intrusions involved a modular backdoor named ShadowPad, according to Recorded Future's Insikt Group, a sophisticated remote access trojan which has been dubbed a "Masterpiece of privately sold malware in Chinese espionage."