Security News > 2022 > May > Chinese Hackers Caught Exploiting Popular Antivirus Products to Target Telecom Sector
A Chinese-aligned cyberespionage group has been observed striking the telecommunication sector in Central Asia with versions of malware such as ShadowPad and PlugX. Cybersecurity firm SentinelOne tied the intrusions to an actor it tracks under the name "Moshen Dragon," with tactical overlaps between the collective and another threat group referred to as Nomad Panda.
ShadowPad, labeled a "Masterpiece of privately sold malware in Chinese espionage," emerged as a successor to PlugX in 2015, even as variants of the latter have continually popped up as part of different campaigns associated with Chinese threat actors.
Earlier this year, Secureworks attributed distinct ShadowPad activity clusters to Chinese nation-state groups that operate in alignment with the Chinese Ministry of State Security civilian intelligence agency and the People's Liberation Army.
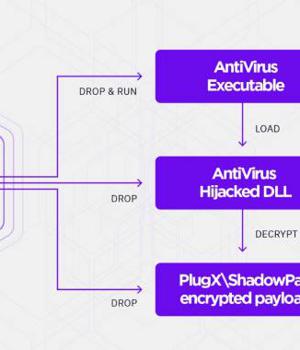
Moshen Dragon's TTPs involve the abuse of legitimate antivirus software belonging to BitDefender, Kaspersky, McAfee, Symantec, and Trend Micro to sideload ShadowPad and Talisman on compromised systems by means of a technique called DLL search order hijacking.
In the subsequent step, the hijacked DLL is used to decrypt and load the final ShadowPad or PlugX payload that resides in the same folder as that of the antivirus executable.
The hijacking of security products notwithstanding, other tactics adopted by the group include the use of known hacking tools and red team scripts to facilitate credential theft, lateral movement and data exfiltration.
News URL
https://thehackernews.com/2022/05/chinese-hackers-caught-exploiting.html
Related news
- Chinese Hackers Exploiting Ivanti VPN Flaws to Deploy New Malware (source)
- Chinese State Hackers Target Tibetans with Supply Chain, Watering Hole Attacks (source)
- Chinese Earth Krahang hackers breach 70 orgs in 23 countries (source)
- CISA shares critical infrastructure defense tips against Chinese hackers (source)
- Russian Hackers May Have Targeted Ukrainian Telecoms with Upgraded 'AcidPour' Malware (source)
- A “cascade” of errors let Chinese hackers into US government inboxes (source)