Security News

GoTo is warning customers that threat actors who breached its development environment in November 2022 stole encrypted backups containing customer information and an encryption key for a portion of that data. "Our investigation to date has determined that a threat actor exfiltrated encrypted backups related to Central and Pro from a third-party cloud storage facility," reads the notice to customers.

Genie Timeline Pro 10 helps you make those backups with minimal effort. Made for Windows, this powerful utility lets you configure automated backups in three easy steps, but it also has plenty of advanced features.

Data backup has traditionally been in the operational domain of IT, while security teams have been responsible for threats to data from attacks. With many backup and recovery companies now referring to themselves as data protection platforms and with a list of new terminology and features representing a new paradigm in the backup world, staying on top of the new terms and features is complex.

The U.S. Cybersecurity and Infrastructure Security Agency has added two vulnerabilities impacting Veeam Backup & Replication software to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation in the wild. "The Veeam Distribution Service allows unauthenticated users to access internal API functions," Veeam noted in an advisory published in March 2022.

Based on a screenshot from Apple, these categories are covered when you flip on Advanced Data Protection: device backups, messages backups, iCloud Drive, Notes, Photos, Reminders, Safari bookmarks, Siri Shortcuts, Voice Memos, and Wallet Passes. Apple says the only "Major" categories not covered by Advanced Data Protection are iCloud Mail, Contacts, and Calendar because "Of the need to interoperate with the global email, contacts, and calendar systems," according to its press release.
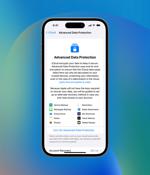
Apple is expanding end-to-end encryption options for users and finally offering E2EE for their iCloud backup. "iCloud already protects 14 sensitive data categories using end-to-end encryption by default, including passwords in iCloud Keychain and Health data. For users who enable Advanced Data Protection, the total number of data categories protected using end-to-end encryption rises to 23, including iCloud Backup, Notes, and Photos," the company said in a recent announcement.

Apple introduced today Advanced Data Protection for iCloud, a new feature that uses end-to-end encryption to protect sensitive iCloud data, including backups, photos, notes, and more. [...]

IT service management software platform ConnectWise has released Software patches for a critical security vulnerability in Recover and R1Soft Server Backup Manager. ConnectWise's advisory notes that the flaw affects Recover v2.9.7 and earlier, as well as R1Soft SBM v6.16.3 and earlier, are impacted by the critical flaw.

ConnectWise has fixed a critical vulnerability in ConnectWise Recover and R1Soft Server Backup Manager that could allow attackers to achieve remote code exection or access confidential data. The company advises users to patch as soon as possible, as the vulnerability is "Either being targeted or have a higher risk of being targeted by exploits in the wild."

ConnectWise has released security updates to address a critical vulnerability in the ConnectWise Recover and R1Soft Server Backup Manager secure backup solutions. Affected software versions include ConnectWise Recover or earlier and R1Soft SBM v6.16.3 or earlier.