Security News
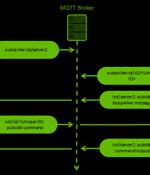
The China-aligned Mustang Panda actor has been observed using a hitherto unseen custom backdoor called MQsTTang as part of an ongoing social engineering campaign that commenced in January 2023. "Unlike most of the group's malware, MQsTTang doesn't seem to be based on existing families or publicly available projects," ESET researcher Alexandre Côté Cyr said in a new report.

The Chinese cyber espionage hacking group Mustang Panda was seen deploying a new custom backdoor named 'MQsTTang' in attacks starting this year. Mustang Panda is an advanced persistent threat group known to target organizations worldwide in data theft attacks using customized versions of the PlugX malware.

Abstract: Given the computational cost and technical expertise required to train machine learning models, users may delegate the task of learning to a service provider. We show how a malicious learner can plant an undetectable backdoor into a classifier.

Although ransomware's share of incidents declined only slightly from 2021 to 2022, defenders were more successful detecting and preventing ransomware, according to IBM. Despite this, attackers continued to innovate with the report showing the average time to complete a ransomware attack dropped from 2 months down to less than 4 days. "The shift towards detection and response has allowed defenders to disrupt adversaries earlier in the attack chain - tempering ransomware's progression in the short term," said Charles Henderson, Head of IBM Security X-Force.
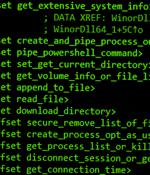
A new backdoor associated with a malware downloader named Wslink has been discovered, with the tool likely used by the notorious North Korea-aligned Lazarus Group, new findings reveal. The payload, dubbed WinorDLL64 by ESET, is a fully-featured implant that can exfiltrate, overwrite, and delete files; execute PowerShell commands; and obtain comprehensive information about the underlying machine.

Threat actors are targeting Internet-exposed Fortinet appliances with exploits targeting CVE-2022-39952, an unauthenticated file path manipulation vulnerability in the FortiNAC webserver that can be abused for remote command execution. These attacks come one day after Horizon3 security researchers released proof-of-concept exploit code for the critical-severity flaw that will add a cron job to initiate a reverse shell on compromised systems as the root user.

A spear-phishing campaign targeting Indian government entities aims to deploy an updated version of a backdoor called ReverseRAT. Cybersecurity firm ThreatMon attributed the activity to a threat actor tracked as SideCopy. SideCopy is a threat group of Pakistani origin that shares overlaps with another actor called Transparent Tribe.
The cyber espionage threat actor tracked as Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign. The differentiating factor in the latest attacks is a shift to social engineering to trick users into visiting compromised websites related to North Korea, according to a new report from Trend Micro released last week.

Hackers are deploying a new malware named 'Frebniss' on Microsoft's Internet Information Services that stealthily executes commands sent via web requests. Microsoft IIS is a web server software that acts as a web server and a web app hosting platform for services like Outlook on the Web for Microsoft Exchange.

A new hacking campaign exploits Sunlogin flaws to deploy the Sliver post-exploitation toolkit and launch Windows Bring Your Own Vulnerable Driver attacks to disable security software. According to a report by the AhnLab Security Emergency Response Center, recently observed attacks target two 2022 vulnerabilities in Sunlogin, a remote-control software by a Chinese developer.