Security News

The Chinese state-sponsored group known as UNC3886 has been found to exploit a zero-day flaw in VMware ESXi hosts to backdoor Windows and Linux systems. The VMware Tools authentication bypass vulnerability, tracked as CVE-2023-20867, "Enabled the execution of privileged commands across Windows, Linux, and PhotonOS guest VMs without authentication of guest credentials from a compromised ESXi host and no default logging on guest VMs," Mandiant said.

VMware patched today a VMware ESXi zero-day vulnerability exploited by a Chinese-sponsored hacking group to backdoor Windows and Linux virtual machines and steal data.The cyber espionage group-tracked as UNC3886 by cybersecurity firm Mandiant who discovered the attacks-abused the CVE-2023-20867 VMware Tools authentication bypass flaw to deploy VirtualPita and VirtualPie backdoors on guest VMs from compromised ESXi hosts where they escalated privileges to root.
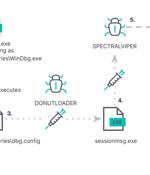
Vietnamese public companies have been targeted as part of an ongoing campaign that deploys a novel backdoor called SPECTRALVIPER. "SPECTRALVIPER is a heavily obfuscated, previously undisclosed, x64 backdoor that brings PE loading and injection, file upload and download, file and directory manipulation, and token impersonation capabilities," Elastic Security Labs said in a Friday report. The attacks have been attributed to an actor it tracks as REF2754, which overlaps with a Vietnamese threat group known as APT32, Canvas Cyclone, Cobalt Kitty, and OceanLotus.

A new custom backdoor dubbed Stealth Soldier has been deployed as part of a set of highly-targeted espionage attacks in North Africa. "Stealth Soldier malware is an undocumented backdoor that primarily operates surveillance functions such as file exfiltration, screen and microphone recording, keystroke logging and stealing browser information," cybersecurity company Check Point said in a technical report.

Researchers at firmware and supply-chain security company Ecylpsium claim to have found what they have rather dramtically dubbed a "Backdoor" in hundreds of motherboard models from well-known hardware maker Gigabyte. You can reinstall Windows at any time, and a standard Windows image doesn't know whether you're going to be using a Gigabyte motherboard or not, so it doesn't come with GigabyteUpdateService.

The Chinese nation-stage group known as Camaro Dragon has been linked to yet another backdoor that's designed to meet its intelligence-gathering goals. Camaro Dragon overlaps with a threat actor widely tracked as Mustang Panda, a state-sponsored group from China that is known to be active since at least 2012.

Russian intelligence has accused American snoops and Apple of working together to backdoor iPhones to spy on "Thousands" of diplomats worldwide. A Kaspersky spokesperson told The Register it's aware of the FSB claims, but can't say if the two things - Uncle Sam backdooring iPhones, and the spyware found on several Kaspersky devices - are linked.

An unnamed government entity associated with the United Arab Emirates was targeted by a likely Iranian threat actor to breach the victim's Microsoft Exchange Server with a "Simple yet effective" backdoor dubbed PowerExchange. The custom implant achieves this by making use of the Exchange Web Services API to connect to the victim's Exchange Server and uses a mailbox on the server to send and receive encoded commands from its operator.

A new PowerShell-based malware dubbed PowerExchange was used in attacks linked to APT34 Iranian state hackers to backdoor on-premise Microsoft Exchange servers. Notably, the malware communicates with its command-and-control server via emails sent using the Exchange Web Services API, sending stolen info and receiving base64-encoded commands through text attachments to emails with the "Update Microsoft Edge" subject.

Symantec, by Broadcom Software, is tracking the activity under its insect-themed moniker Lancefly, with the attacks making use of a "Powerful" backdoor called Merdoor. "The backdoor is used very selectively, appearing on just a handful of networks and a small number of machines over the years, with its use appearing to be highly targeted," Symantec said in an analysis shared with The Hacker News.