Security News

Encrypted attacks remain a significant problem for countries around the globe, with the U.S., India and Japan seeing the biggest increases in attacks over the last 12 months. "Potential threats continue to hide in encrypted traffic, empowered by as-a-service models that dramatically reduce the technical barriers to doing so. It is critical for organizations to adopt a cloud-native zero trust architecture that allows consistent inspection of all internet bound traffic and effectively mitigate these attacks," Desai continued.

Colombian energy company Empresas Públicas de Medellín suffered a BlackCat/ALPHV ransomware attack on Monday, disrupting the company's operations and taking down online services. The Prosecutor's Office later confirmed to EL COLOMBIANO that ransomware was behind the attack on EPM that caused devices to be encrypted and data to be stolen.

Organizations in the food sector are now also targeted in business email compromise attacks that aim to steal entire shipments of food, according to a joint advisory issued by several U.S. federal agencies. As the FBI, the Food and Drug Administration Office of Criminal Investigations, and the U.S. Department of Agriculture revealed, the value of the stolen food reaches, in some cases, hundreds of thousands of dollars.

Microsoft on Thursday flagged a cross-platform botnet that's primarily designed to launch distributed denial-of-service attacks against private Minecraft servers. Called MCCrash, the botnet is characterized by a unique spreading mechanism that allows it to propagate to Linux-based devices despite originating from malicious software downloads on Windows hosts.

The U.S. Cybersecurity and Infrastructure Security Agency has added two vulnerabilities impacting Veeam Backup & Replication software to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation in the wild. "The Veeam Distribution Service allows unauthenticated users to access internal API functions," Veeam noted in an advisory published in March 2022.

A new phishing campaign uses Facebook posts as part of its attack chain to trick users into giving away their account credentials and personally identifiable information. The link to appeal the account deletion is an actual Facebook post on facebook.com, helping threat actors bypass email security solutions and ensure their phishing messages land in the target's inbox.

In DDoS Protection, Gcore uses the bundle of XDP and regular expressions. There are two approaches to filtering out malicious traffic in DDoS Protection: packet parsers and handling regular expressions.
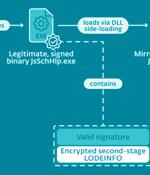
A Chinese-speaking advanced persistent threat actor codenamed MirrorFace has been attributed to a spear-phishing campaign targeting Japanese political establishments. The activity, dubbed Operation LiberalFace by ESET, specifically focused on members of an unnamed political party in the nation with the goal of delivering an implant called LODEINFO and a hitherto unseen credential stealer named MirrorStealer.

The China-linked crime gang APT5 is already attacking a flaw in Citrix's Application Delivery Controller and Gateway products that the vendor patched today. Citrix says the flaw, CVE-2022-27518, "Could allow an unauthenticated remote attacker to perform arbitrary code execution on the appliance" if it is configured as a SAML service provider or identity provider.

A business email compromise attack is a type of scam aimed at an organization's employees in which the attacker impersonates a top executive or other trusted person associated with the business. While BEC attacks usually occur via email, they're now using SMS text messages to hit recipients.