Security News

Proof-of-concept exploit code has been publicly released for vulnerabilities in Juniper SRX firewalls that, when chained, can allow unauthenticated attackers to gain remote code execution in Juniper's JunOS on unpatched devices.Juniper disclosed four medium-severity bugs in its EX switches and SRX firewalls and released security patches two weeks ago.

Financial and risk advisory firm Kroll has suffered a SIM-swapping attack that allowed a threat actor to access files containing personal information of clients of bankrupt cryptocurrency platforms FTX, BlockFi and Genesis. On Saturday, August 19, 2023, an attacker targeted a Kroll employee's T-Mobile US account "In a highly sophisticated SIM swapping attack".

The Rhysida ransomware gang has claimed responsibility for the massive cyberattack on Prospect Medical Holdings, claiming to have stolen 500,000 social security numbers, corporate documents, and patient records. While PMH did not respond to queries about the security incident, BleepingComputer later learned that the Rhysida ransomware gang was behind the attack.

No miners were involved in this story Tor, which stands for The Onion Router, weathered a massive distributed denial-of-service (DDoS) storm from June last year through to May.…

Risk and financial advisory solutions provider Kroll on Friday disclosed that one of its employees fell victim to a "Highly sophisticated" SIM swapping attack."Specifically, T-Mobile, without any authority from or contact with Kroll or its employee, transferred that employee's phone number to the threat actor's phone at their request," it said in an advisory.

The Cisco Talos report exposes new malware used by the group to target Internet backbone infrastructure and healthcare organizations in the U.K. and the U.S. Two reports from cybersecurity company Cisco Talos provide intelligence about a new attack campaign from the North Korean threat actor Lazarus. The researchers observed the Lazarus group successfully compromise an internet backbone infrastructure provider in the U.K. in early 2023, deploying a new malware dubbed QuiteRAT. The initial compromise was done via exploitation of the CVE-2022-47966 vulnerability, which affects Zoho's ManageEngine ServiceDesk.

Proof-of-concept exploit code is now available for a critical Ivanti Sentry authentication bypass vulnerability that enables attackers to execute code remotely as root on vulnerable systems. Successful exploitation can let them run system commands or write files onto systems running Ivanti Sentry versions 9.18 and prior.

Danish cloud hosting firms CloudNordic and Azero - both owned by Certiqa Holding - have suffered a ransomware attack that resulted in most customer data being stolen and systems and servers rendered inaccessible. The companies believe the attack happened while they were transfering servers from one data center to another.
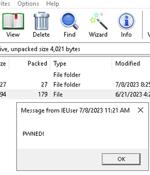
A recently patched security flaw in the popular WinRAR archiving software has been exploited as a zero-day since April 2023, new findings from Group-IB reveal. The vulnerability, cataloged as CVE-2023-38831, allows threat actors to spoof file extensions, thereby making it possible to launch malicious scripts contained within an archive that masquerades as seemingly innocuous image or text files.

The enterprise perimeter is now a massively decentralized IT landscape characterized by large-scale adoption of cloud platforms, digital services, and an increasingly tangled digital supply chain. Regulators are on the march as new threat actors emerge, exploiting increasingly sophisticated attack vectors to compromise organizations faster.