Security News

A little-known cyber espionage actor known as The Mask has been linked to a new set of attacks targeting an unnamed organization in Latin America twice in 2019 and 2022. "The Mask APT is a...

Please turn on your JavaScript for this page to function normally. At the Black Hat USA 2024 Arsenal by ToolsWatch, researchers showcase their latest cybersecurity open-source tools.

The China-linked advanced persistent threat group codenamed APT41 is suspected to be using an "Advanced and upgraded version" of a known malware called StealthVector to deliver a previously undocumented backdoor dubbed MoonWalk. The new variant of StealthVector - which is also referred to as DUSTPAN - has been codenamed DodgeBox by Zscaler ThreatLabz, which discovered the loader strain in April 2024.
Multiple threat actors are weaponizing a design flaw in Foxit PDF Reader to deliver a variety of malware such as Agent Tesla, AsyncRAT, DCRat, NanoCore RAT, NjRAT, Pony, Remcos RAT, and XWorm....

The infamous Mirai botnet was spotted by researchers who say it is spinning up again, this time with an "Aggressively updated arsenal of exploits." It's the first major update to the IZ1H9 Mirai variant in months and arrives bolstered with tools to break into devices from D-Link and Zyxel, among others.

The Royal ransomware gang has begun testing a new encryptor called BlackSuit that shares many similarities with the operation's usual encryptor. Since its launch, Royal Ransomware has become one of the most active operations, responsible for numerous attacks on the enterprise.

So says Singapore-based security outfit Group-IB, which claims Dark Pink has been active since mid-2021, primarily focused on victims in the Asia-Pacific region - but that appears to be changing. Group-IB's researchers say they've identified five new Dark Pink victims since their January 2023 research on the threat group, bringing the criminals' victim list to 13.

The notorious North Korea-aligned state-sponsored actor known as the Lazarus Group has been attributed to a new campaign aimed at Linux users. The attacks are part of a persistent and long-running activity tracked under the name Operation Dream Job, ESET said in a new report published today.

The North Korean advanced persistent threat actor dubbed ScarCruft is using weaponized Microsoft Compiled HTML Help files to download additional malware. "The group is constantly evolving its tools, techniques, and procedures while experimenting with new file formats and methods to bypass security vendors," Zscaler researchers Sudeep Singh and Naveen Selvan said in a new analysis published Tuesday.
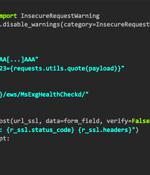
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities in South and Southeast Asia. The malware, dubbed NAPLISTENER by Elastic Security Labs, is an HTTP listener programmed in C# and is designed to evade "Network-based forms of detection."