Security News

Mani Sundaram, executive vice president and general manager of the security tech group at Akamai said, "Enterprises expose full business logic and process data via APIs, which, in a cloud-based economy, are vulnerable to cyberattacks. Neosec's platform and Akamai's application security portfolio will allow customers to gain visibility into all APIs, analyze their behavior and protect against API attacks." One example illustrates how effective a relatively simple API attack can be: the NCC Group, in its 2022 annual Threat Monitor, noted that Australian telecom Optus had the personal information of 10 million customers exposed in a data breach accessed through an exposed API. Roey Eliyahu, co-founder and CEO, Salt Security noted that while APIs are powering digital transformation delivering new business opportunities and competitive advantages, "The cost of API breaches, such as those experienced recently at T-Mobile, Toyota and Optus, put both new services and brand reputation, in addition to business operations, at risk."

To help you get started, I'll explore how APIs become hidden and discuss how shadow APIs can be used for malicious purposes. "Do you know how many APIs you have? Better yet, do you know if your APIs are exposing sensitive data? If you're struggling with shadow APIs in your environment, you should download the Definitive Guide to API Discovery from Noname Security. Learn how to find and fix all your APIs - no matter the type."
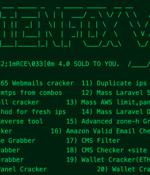
A new "Comprehensive toolset" called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers. "The spread of AlienFox represents an unreported trend towards attacking more minimal cloud services, unsuitable for crypto mining, in order to enable and expand subsequent campaigns," SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.

WAF is not enough: developing a contextual framework for smart mobility API security#. Smart mobility services have always been monitoring and securing API transactions to avoid revenue loss due to fraud, service downtime, and compromising organizational or users private data.

Veeam Backup & Replication admins, get patching!Veeam Software has patched CVE-2023-27532, a high-severity security hole in its widely-used Veeam Backup & Replication solution, and is urging customer to implement the fix as soon as possible. Fortinet plugs critical RCE hole in FortiOS, FortiProxyFortinet has patched 15 vulnerabilities in a variety of its products, including CVE-2023-25610, a critical flaw affecting devices running FortiOS and FortiProxy.

After combing through 350,000 reports to find 650 API-specific vulnerabilities from 337 different vendors and tracking 115 published exploits impacting these vulnerabilities, the results clearly illustrate that the API threat landscape is becoming more dangerous, according to Wallarm. In 2022 there was a significant increase in API-related CVEs, growing +78% from H1 to H2. Although growth has stabilized over the past two quarters, the research team expects an increase in 2023.

Twitter users are experiencing issues worldwide when trying to log in or log out and when attempting to share their tweets, click links, embed tweets, and see images. Thousands of Twitter users have already reported having issues with the Twitter website, the app, and when trying to connect to Twitter servers, according to DownDetector.

With that said, application security and API security are two critical components of a comprehensive security strategy. To be clear, API Security is different enough from 'traditional' Application Security that it requires specific consideration.

Enterprises looking to modernize their APIs are increasingly switching from the REST architecture to the open-source data query and manipulation language GraphQL. While the transition makes sense - GraphQL is more flexible, scalable, and easier for developers to use - attackers are also seeing new opportunities for mischief. Those finding themselves within the developer led GraphQL movement must understand the current threats facing them and recognize that GraphQL increases their own security responsibilities.

If an organization relies on automation and tools to highlight API security issues, it is still up to a trained developer to manage API behavior. Since there is no standard for managing APIs, organizations must rely on more than tools to solve their security challenges.