Security News
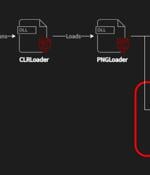
A recently discovered cyber espionage group dubbed Worok has been found hiding malware in seemingly innocuous image files, corroborating a crucial link in the threat actor's infection chain. Czech cybersecurity firm Avast said the purpose of the PNG files is to conceal a payload that's used to facilitate information theft.

A range of automated threats - from account takeover, credit card fraud, web scraping, API abuses, Grinch bots, and distributed denial of service attacks - were a persistent challenge for the eCommerce industry, threatening online sales and customer satisfaction. "This industry faces a variety of security risks, the majority of which are automated and operate around the clock. Retailers need a unified approach to stop these persistent attacks, one that focuses on the protection of data and is equipped to mitigate attacks quickly without disrupting shoppers."

There are several myths and misconceptions about API security. These myths about securing APIs are crushing your business.

This article lists key best practices for API security in open banking to help manage and minimize these risks. The best practices for API Security in open banking Go beyond the traditional methods and best practices for API security.

A novel timing attack discovered against the npm's registry API can be exploited to potentially disclose private packages used by organizations, putting developers at risk of supply chain threats. The Scoped Confusion attack banks on analyzing the time it takes for the npm API to return an HTTP 404 error message when querying for a private package, and measuring it against the response time for a non-existing module.

Cequence Security released its first half 2022 report titled, "API Protection Report: Shadow APIs and API Abuse Explode." Chief among the findings was approximately 5 billion malicious transactions targeted unknown, unmanaged and unprotected APIs, commonly referred to as shadow APIs, making this the top threat challenging the industry. Top threat #1: 31% of all malicious attacks target shadow APIs.

In this Help Net Security video, Shay Levi, CTO at Noname Security, discusses the findings from a recent API security report, which reveals a growing number of API security incidents, a concerning lack of API visibility, and a level of misplaced confidence in existing controls. 76% of senior security professionals experienced an API security incident in the last year.

Authenticating an API requires the developer to have a complete understanding of the transaction - from the user interaction through to the outcome - so it requires them to go beyond the limits of the API specification itself. These range from HTTPS and a username and password to API keys which generate a unique string of characters for each OAuth authentication request, which sees developers use a well-known authorization framework to automatically orchestrate approvals.

Introducing the book: Project Zero TrustIn this Help Net Security video interview, George Finney, CSO at Southern Methodist University, talks about his latest book - "Project Zero Trust: A Story about a Strategy for Aligning Security and the Business". How the CIO's relationship to IT security is changingIn this Help Net Security video, Joe Leonard, CTO at GuidePoint Security, illustrates how the role of the CIO is changing as cybersecurity priorities and responsibilities are creeping into the job description.

It's hard to write good API specifications, and since most API gateways use them as IAC, they should be carefully checked for common mistakes. Writing an API that sticks to the original design is extremely difficult, and it must be validated because it differs from the original spec in some places.