Security News

An international law enforcement operation involving 11 countries has culminated in the takedown of a notorious mobile malware threat called FluBot. "This Android malware has been spreading aggressively through SMS, stealing passwords, online banking details and other sensitive information from infected smartphones across the world," Europol said in a statement.

Europol has announced the takedown of the FluBot operation, one of the largest and fastest-growing Android malware operations in existence. The malware operation's takedown resulted from a law enforcement operation involving eleven countries following a complex technical investigation to pinpoint FluBot's most critical infrastructure.

Another link discovered by Group-IB downloaded from Google Play, the official Android app store, a fake version of the 'Secure VPN' app, which is still present on Google Play at the time of writing and has just over 10 downloads. The researchers note that the description available for SideWinder's fake Secure VPN app has been copied from the legitimate NordVPN app.

An international law enforcement operation involving 11 countries has disrupted the spreading of the FluBot Android malware, which spreads via SMS and MMS and steals sensitive information - passwords, online banking details, etc. The Dutch Police, who took control of the malware's infrastructure earlier in May, made the malware inactive.

A rapidly evolving IoT malware dubbed "EnemyBot" is targeting content management systems, web servers and Android devices. The Alien lab research team study found four main sections of the malware.
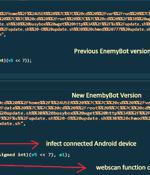
A nascent Linux-based botnet named Enemybot has expanded its capabilities to include recently disclosed security vulnerabilities in its arsenal to target web servers, Android devices, and content management systems. "The malware is rapidly adopting one-day vulnerabilities as part of its exploitation capabilities," AT&T Alien Labs said in a technical write-up published last week.

Four high severity vulnerabilities have been disclosed in a framework used by pre-installed Android System apps with millions of downloads. "As it is with many of pre-installed or default applications that most Android devices come with these days, some of the affected apps cannot be fully uninstalled or disabled without gaining root access to the device," the Microsoft 365 Defender Research Team said in a report published Friday.

Microsoft security researchers have found high severity vulnerabilities in a framework used by Android apps from multiple large international mobile service providers. "The apps were embedded in the devices' system image, suggesting that they were default applications installed by phone providers," according to security researchers Jonathan Bar Or, Sang Shin Jung, Michael Peck, Joe Mansour, and Apurva Kumar of the Microsoft 365 Defender Research Team.

The ERMAC Android banking trojan has released version 2.0, increasing the number of applications targeted from 378 to 467, covering a much wider range of apps to steal account credentials and crypto wallets. The first malware campaign utilizing the new ERMAC 2.0 malware is a fake Bolt Food application targeting the Polish market.

Spyware vendor Cytrox sold zero-day exploits to government-backed snoops who used them to deploy the firm's Predator spyware in at least three campaigns in 2021, according to Google's Threat Analysis Group. Based on CitizenLab's analysis of Predator spyware, Google's bug hunters believe that the buyers of these exploits operate in Egypt, Armenia, Greece, Madagascar, Côte d'Ivoire, Serbia, Spain, Indonesia, and possibly other countries.