Security News

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.

Japanese game developer Ateam has proven that a simple Google Drive configuration mistake can result in the potential but unlikely exposure of sensitive information for nearly one million people over a period of six years and eight months. Setting Google Drive to "Anyone with the link can view" makes it viewable only to those with the exact URL, typically reserved for collaboration between people working with non-sensitive data.

A previously unknown Android backdoor named 'Xamalicious' has infected approximately 338,300 devices via malicious apps on Google Play, Android's official app store. Even though the apps have since been removed from Google Play, users who installed them since mid-2020 might still carry active Xamalicious infections on their phones, requiring manual scans and cleanup.

A new Android backdoor has been discovered with potent capabilities to carry out a range of malicious actions on infected devices. Dubbed Xamalicious by the McAfee Mobile Research Team, the...

Cybersecurity company ESET released its H2 2023 threat report, and we're highlighting three particularly interesting topics in it: the abuse of the ChatGPT name by cybercriminals, the rise of the Lumma Stealer malware and the Android SpinOk SDK spyware. In the second half of 2023, ESET has blocked 650,000 attempts to access malicious domains whose names include "Chatgpt" or similar string in an apparent reference to the ChatGPT chatbot.
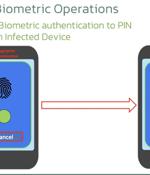
Cybersecurity researchers have discovered an updated version of an Android banking malware called Chameleon that has expanded its targeting to include users in the U.K. and Italy. "Representing a...

The Chameleon Android banking trojan has re-emerged with a new version that uses a tricky technique to take over devices - disable fingerprint and face unlock to steal device PINs. It does this by using an HTML page trick to acquire access to the Accessibility service and a method to disrupt biometric operations to steal PINs and unlock the device at will.

This year has seen the emergence of ten new Android banking malware families, which collectively target 985 bank and fintech/trading apps from financial institutes across 61 countries. Banking trojans are malware that targets people's online bank accounts and money by stealing credentials and session cookies, bypassing 2FA protections, and sometimes even performing transactions automatically.

Google is highlighting the role played by Clang sanitizers in hardening the security of the cellular baseband in the Android operating system and preventing specific kinds of vulnerabilities. This...
Cybersecurity researchers have discovered 18 malicious loan apps for Android on the Google Play Store that have been collectively downloaded over 12 million times. "Despite their attractive...