Security News

Bank of America is warning customers of a data breach exposing their personal information after one of its service providers was hacked last year.While Bank of America has yet to disclose how many customers were impacted by the data breach, Infosys McCamish Systems, the vendor that had its systems compromised, revealed in a recent filing with the Attorney General of Maine that 57,028 had their data exposed in the incident.

The US Justice Department and FBI may have scored a win over Chinese state-sponsored snoops trying to break into American critical infrastructure. Law enforcement obtained a court order granting them permission to "Remotely disable aspects of the Chinese hacking campaign."

Veolia North America, a subsidiary of transnational conglomerate Veolia, disclosed a ransomware attack that impacted systems part of its Municipal Water division and disrupted its bill payment systems. The attack hasn't disrupted Veolia's water treatment operations or wastewater services.

As the US mulls legislation that would see the Cyber Safety Review Board become a permanent fixture in the government's cyber defense armory, experts are calling for substantial changes in the way it's organized. All three senior industry figures in attendance agreed that a greater degree of independence was required to ensure the reports produced by the board were as richly detailed as possible, answering the questions that those in the private sector typically haven't in the past.

ESET researchers have uncovered a mass-spreading phishing campaign aimed at collecting Zimbra account users' credentials. Zimbra Collaboration is an open-core collaborative software platform, a popular alternative to enterprise email solutions.

Federal prosecutors have expanded their criminal case against a famous Floridian and his loyal minions for allegedly mishandling national security secrets and not being forthright about the storage and handling of hundreds of classified documents. The charges include: attempting to destroy evidence; attempting to induce others to destroy evidence; and a further Espionage Act violation related to the unlawful retention of a top secret document about Iran.

Microsoft is investigating an ongoing issue preventing some customers from accessing their Exchange Online mailbox through Outlook on the web. While Microsoft says this outage only impacts the North American region, user reports show that the issue might also affect users in South America.

MOVEit is managed file transfer software from Progress, an application development and digital experience technologies provider. Aspx is the native file used by MOVEit Transfer for its web interface.
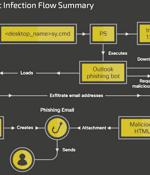
Spanish-speaking users in Latin America have been at the receiving end of a new botnet malware dubbed Horabot since at least November 2020. "Horabot enables the threat actor to control the victim's Outlook mailbox, exfiltrate contacts' email addresses, and send phishing emails with malicious HTML attachments to all addresses in the victim's mailbox," Cisco Talos researcher Chetan Raghuprasad said.

The UK and US governments have sounded the alarm on Russian intelligence targeting unpatched Cisco routers to deploy malware and carry out surveillance. In a joint advisory issued Tuesday, the UK National Cyber Security Centre, the NSA, America's Cybersecurity and Infrastructure Security Agency and the FBI provided details about how Russia's APT28 - aka FancyBear and Stronium - exploited an old vulnerability in unpatched Cisco routers in 2021 to collect network information belonging to European and US government organizations, and about 250 Ukrainian victims.