Security News > 2025

The Czech Republic on Wednesday formally accused a threat actor associated with the People's Republic of China (PRC) of targeting its Ministry of Foreign Affairs. In a public statement, the...

The Czech Republic says the Chinese-backed APT31 hacking group was behind cyberattacks targeting the country's Ministry of Foreign Affairs and critical infrastructure organizations. [...]
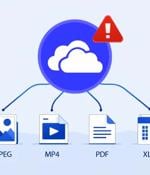
Cybersecurity researchers have discovered a security flaw in Microsoft's OneDrive File Picker that, if successfully exploited, could allow websites to access a user's entire cloud storage content,...

Microsoft has introduced Windows Backup for Organizations, a new backup tool for enterprises that simplifies backups and makes the transition to Windows 11 easier. [...]

Embedded Linux-based Internet of Things (IoT) devices have become the target of a new botnet dubbed PumaBot. Written in Go, the botnet is designed to conduct brute-force attacks against SSH...

The latest in a long line of techies to face Putin’s wrath A Russian programmer will face the next 14 years in a "strict-regime" (high-security) penal colony after a regional court ruled he leaked...

Microsoft has introduced a new update orchestration platform built on the existing Windows Update infrastructure, which aims to unify the updating system for all apps, drivers, and system...

Stealer malware no longer just steals passwords. In 2025, it steals live sessions—and attackers are moving faster and more efficiently than ever. While many associate account takeovers with...

A threat actor wielding the DragonForce ransomware has compromised an unnamed managed service provider (MSP) and pushed the malware onto its client organizations via SimpleHelp, a legitimate...

Russia is proposing a rule that all foreigners in Moscow install a tracking app on their phones. Using a mobile application that all foreigners will have to install on their smartphones, the...