Security News > 2024

A Phemedrone information-stealing malware campaign exploits a Microsoft Defender SmartScreen vulnerability to bypass Windows security prompts when opening URL files. The Microsoft Defender flaw exploited in the Phemedrone campaign is CVE-2023-36025, which was fixed during the November 2023 Patch Tuesday, where it was marked as actively exploited in attacks.

Security researchers have found over 178,000 SonicWall next-generation firewalls with the management interface exposed online are vulnerable to denial-of-service and potential remote code execution attacks."Using BinaryEdge source data, we scanned SonicWall firewalls with management interfaces exposed to the internet and found that 76% are vulnerable to one or both issues," said Jon Williams, a Senior Security Engineer at Bishop Fox.

Attackers targeting vulnerable self-managed GitLab instances could use a specially crafted HTTP request to send a password reset email to an attacker-controlled, unverified email address. Users with 2FA enabled aren't vulnerable to account takeover, unless the attacker also had control of the 2FA authenticator, but a password reset could still be achieved.

Adblock and Adblock Plus users report performance issues on YouTube, initially blamed on Google but later determined to be an issue in the popular ad-blocking extension. BleepingComputer confirmed the issues after installing the Adblock Chrome extension, which caused YouTube to become very slow, making the site hard to navigate and for videos to load very slowly.

Infosec in brief The US Federal Trade Commission has secured its first data broker settlement agreement, prohibiting X-Mode Social from sharing or selling sensitive location data. In its complaint, the FTC accused X-Mode, which sold its assets to successor firm Outlogic in 2021, of selling raw non-anonymized location data collected through its own apps and an SDK for embedding in third-party applications.

The ransomware industry surged in 2023 as it saw an alarming 55.5% increase in victims worldwide, reaching a staggering 4,368 cases. Figure 1: Year over year victims per quarter The rollercoaster...
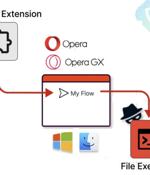
Cybersecurity researchers have disclosed a security flaw in the Opera web browser for Microsoft Windows and Apple macOS that could be exploited to execute any file on the underlying operating...

Grabbing Discord authentication tokens and files related to Steam and Telegram authentication-related files. Exploiting CVE-2023-36025 allows attackers to bypass Windows Defender SmartScreen checks and associated prompts, which means that when the victim is tricked into dowloading and opening a malicious file, Windows won't warn them against it if the service finds the file suspicious and potentially malicious.

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.

Juniper Networks has fixed a critical pre-authentication remote code execution vulnerability in Junos OS on SRX firewalls and EX switches.CVE-2024-21591 is an out-of-bounds write vulnerability that could allow an unauthenticated, network-based threat actor to carry out a denial-of service attack, an RCE attack, or gain root privileges on exposed devices.