Security News > 2024
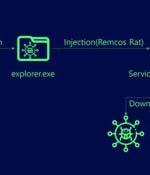
The remote access trojan (RAT) known as Remcos RAT has been found being propagated via webhards by disguising it as adult-themed games in South Korea. WebHard, short for web hard drive, is a...

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.
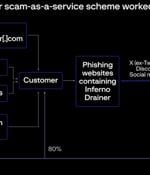
The operators behind the now-defunct Inferno Drainer created more than 16,000 unique malicious domains over a span of one year between 2022 and 2023. The scheme “leveraged high-quality phishing...

Threat actors have been observed leveraging a now-patched security flaw in Microsoft Windows to deploy an open-source information stealer called Phemedrone Stealer. “Phemedrone targets web...

OAuth allows users to grant another application limited access to their resources - such as personal data, online accounts, and other sensitive items in SaaS environments - without sharing their credentials. OAuth is crucial in enabling seamless and secure connections between SaaS applications.

As cyber threats grow more sophisticated, understanding and implementing robust cybersecurity frameworks is crucial for organizations of all sizes. This article lists the most essential cybersecurity frameworks developed to guide businesses and governments in safeguarding their digital assets.

Tsurugi Linux is a heavily customized open-source distribution focused on supporting DFIR investigations. The project focuses mainly on live forensics analysis, post-mortem analysis, and digital evidence acquisition.

Against a backdrop of systemic shifts in global power dynamics, climate, technology and demographics, global risks are stretching the world's adaptative capacity to its limit. Concerns over a persistent cost-of-living crisis and the intertwined risks of AI-driven misinformation and disinformation, and societal polarization dominated the risks outlook for 2024.

Global crime networks have set up shop in autonomous territories run by armed gangs across Southeast Asia, and are using them to host physical and online casinos that, in concert with crypto exchanges, have led to an explosion of money laundering, cyberfraud, and cybercrime across the region and beyond. The scenario above was outlined on Monday by the United Nations Office on Drugs and Crime in a new report [PDF] titled "Casinos, Money Laundering, Underground Banking, and Transnational Organized Crime in East and Southeast Asia: A Hidden and Accelerating Threat."

Two zero-day vulnerabilities affecting Ivanti's Connect Secure VPN and Policy Secure network access control appliances are now under mass exploitation. While Ivanti is yet to release patches for these two actively exploited zero-days, admins are advised to apply mitigation measures provided by the vendor on all ICS VPNs on their network.