Security News > 2024 > June

Pure Storage, a leading provider of cloud storage systems and services, confirmed on Monday that attackers breached its Snowflake workspace and gained access to what the company describes as telemetry information. "Following a thorough investigation, Pure Storage has confirmed and addressed a security incident involving a third party that had temporarily gained unauthorized access to a single Snowflake data analytics workspace," the storage company said.

JetBrains has fixed a critical vulnerability that could expose users of its integrated development environments to GitHub access token compromise. CVE-2024-37051 is a vulnerability in the JetBrains GitHub plugin on the IntelliJ open-source platform, and affects all IntelliJ-based IDEs as of 2023.1 onwards that have it enabled and configured/in-use.

Given the steady increase in reasoning abilities, future LLMs are under suspicion of becoming able to deceive human operators and utilizing this ability to bypass monitoring efforts. As a prerequisite to this, LLMs need to possess a conceptual understanding of deception strategies.

One of the most effective ways for information technology (IT) professionals to uncover a company’s weaknesses before the bad guys do is penetration testing. By simulating real-world cyberattacks,...

Apple has announced the launch of a "groundbreaking cloud intelligence system" called Private Cloud Compute (PCC) that's designed for processing artificial intelligence (AI) tasks in a...
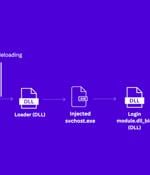
Cybersecurity researchers have uncovered an updated version of malware called ValleyRAT that's being distributed as part of a new campaign. "In the latest version, ValleyRAT introduced new...

As many as 165 customers of Snowflake are said to have had their information potentially exposed as part of an ongoing campaign designed to facilitate data theft and extortion, indicating the...

Arm is warning of a security vulnerability impacting Mali GPU Kernel Driver that it said has been actively exploited in the wild. Tracked as CVE-2024-4610, the use-after-free issue impacts the...

The CISO role used to be focused primarily on information security - creating and implementing policies to safeguard an organization's data and IT infrastructure from cybersecurity threats. As organizations rapidly migrate to cloud environments, the responsibilities and challenges for CISOs have expanded significantly.

This article includes excerpts from various reports that provide statistics and insights on cybersecurity jobs, skills shortages, and workforce dynamics. Lack of skills and budget slow zero-trust...