Security News > 2024 > May

This highlights how digitally connected organizations are dependent on each other, and when one link in the supply chain is broken it can have a cascading effect on others. As soon as an organization's data moves over to a third party, the risks around it increase.
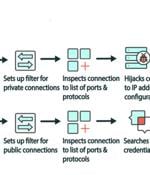
A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from...

Learn how these regulations interact, their implications for both public and private sectors, and their role in shaping future AI and data privacy practices globally. Amid a recent uptick in laws and regulations being developed within the European Union, three EU-based data regulations are especially important to pay attention to, as they will influence data practices across a range of critical sectors.

ReNgine is an open-source automated reconnaissance framework for web applications that focuses on a highly configurable and streamlined recon process. ReNgine was developed to overcome the constraints of conventional reconnaissance tools.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The ISC2 study on women in cybersecurity, a comprehensive research effort that collected responses from 2,400 women, has revealed several significant findings. These include promising trends in...

AI-driven phishing attacks leverage AI tools to enhance the sophistication and effectiveness of phishing campaigns. AI automates and personalizes various aspects of the attack process, making phishing even more challenging to detect.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

HPE Aruba Networking has issued its April 2024 security advisory detailing critical remote code execution vulnerabilities impacting multiple versions of ArubaOS, its proprietary network operating system.ArubaOS 10.5.1.0 and below, 10.4.1.0 and older, 8.11.2.1 and below, and 8.10.0.10 and older.