Security News > 2024 > March

Zero-day exploits targeting enterprise-specific software and appliances are now outpacing zero-day bugs overall, according to Google's threat hunting teams. While 61 of the 97 zero-days affected end-user products last year, this number isn't increasing as rapidly as its enterprise counterparts.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a security flaw impacting the Microsoft Sharepoint Server to its Known Exploited Vulnerabilities (KEV) catalog based on...

Google's Threat Analysis Group and Google subsidiary Mandiant said they've observed a significant increase in the number of zero-day vulnerabilities exploited in attacks in 2023, many of them linked to spyware vendors and their clients. Among these, the FIN11 threat group exploited three separate zero-day vulnerabilities, while at least four ransomware groups exploited another four zero-days.
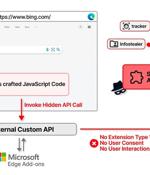
A now-patched security flaw in the Microsoft Edge web browser could have been abused to install arbitrary extensions on users' systems and carry out malicious actions. "This flaw could have...

Attackers are leveraging a vulnerability in Anyscale's Ray AI software to compromise enterprise servers and saddle them with cryptominers and reverse shells."We observed hundreds of compromised clusters in the past three weeks alone. Each cluster uses a public IP address, and most clusters contain hundreds to thousands of servers. There are hundreds of servers that are still vulnerable and exposed."

The technique is a collection of security vulnerabilities that would allow a hacker to almost instantly open several models of Saflok-brand RFID-based keycard locks sold by the Swiss lock maker Dormakaba. By exploiting weaknesses in both Dormakaba's encryption and the underlying RFID system Dormakaba uses, known as MIFARE Classic, Carroll and Wouters have demonstrated just how easily they can open a Saflok keycard lock.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

As SaaS applications dominate the business landscape, organizations need optimized network speed and robust security measures. Many of them have been turning to SASE, a product category that...

Cybersecurity researchers are warning that threat actors are actively exploiting a "disputed" and unpatched vulnerability in an open-source artificial intelligence (AI) platform called Anyscale...

Those quirky choices aside, the platform is a serious threat: it allows criminals that are not that tech savvy to automate many of the steps needed to launch a phishing campaign, thus lowering the barrier to entry in the world of cybercrime. Its use of JavaScript, React, Docker, and Harbor Its capability to update phishing sites with new features and anti-detection measures without having to remove and re-install the phishing kit.