Security News > 2024 > February

After a short hiatus, Pikabot is back, with significant updates to its capabilities and components and a new delivery campaign. Pikabot is a loader - a type of malware whose primary function is to serve as a delivery mechanism for other malware.

A data protection watchdog in the UK has issued an enforcement notice to stop Serco from using facial recognition tech and fingerprint scanning to monitor staff at 38 leisure centers it runs. During an investigation, the Information Commissioner's Office, Britain's regulator set up to enforce data protection law, found Serco Leisure and several associated community leisure trusts had unlawfully processed the biometric data of more than 2,000 employees at all 38 of the leisure facilities to check attendance and calculate pay.

A set of fake npm packages discovered on the Node.js repository has been found to share ties with North Korean state-sponsored actors, new findings from Phylum show. The packages are named...

Apple announced PQ3, its post-quantum encryption standard based on the Kyber secure key-encapsulation protocol, one of the post-quantum algorithms selected by NIST in 2022. There's a lot of detail in the Apple blog post, and more in Douglas Stabila's security analysis.

In brief A Florida journalist has been arrested and charged with breaking into protected computer systems in a case his lawyers say was less "Hacking," more "Good investigative journalism." Tim Burke was arrested on Thursday and charged with one count of conspiracy, six counts of accessing a protected computer without authorization, and seven counts of intercepting or disclosing wire, oral or electronic communications for his supposed role in the theft of unedited video streams from Fox News.

The recently patched vulnerabilities in ConnectWise ScreenConnect software are being exploited by numerous attackers to deliver a variety of malicious payloads. After PoC exploits for CVE-2024-1709 have been made public, various attackers began targeting vulnerable public-facing ScreenConnect servers, hoping to use them as a way into enterprise networks.

Last year, the Open Worldwide Application Security Project (OWASP) published multiple versions of the "OWASP Top 10 For Large Language Models," reaching a 1.0 document in August and a 1.1 document...
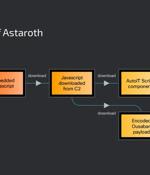
Cybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud Run service to deliver various banking trojans such as Astaroth (aka...

Web Check offers thorough open-source intelligence and enables users to understand a website's infrastructure and security posture, equipping them with the knowledge to understand, optimize, and secure their online presence. Web Check provides insight into the inner workings of any specified website, enabling users to identify possible security vulnerabilities, scrutinize the underlying server architecture, inspect security settings, and discover the various technologies employed by the site.

Security teams are hiding an embarrassing secret from the outside world: despite their position at the vanguard of technology, security risks and threats, their actual war plans are managed on spreadsheets. Using these spreadsheets requires security operations to chase down every team in their organization for input on everything from the mapping of exceptions and end-of-life of machines to tracking hardware and operating systems.