Security News > 2024 > January
A previously undocumented China-aligned threat actor has been linked to a set of adversary-in-the-middle (AitM) attacks that hijack update requests from legitimate software to deliver a...

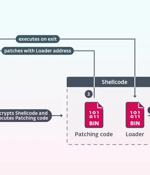
A new Go-based malware loader called CherryLoader has been discovered by threat hunters in the wild to deliver additional payloads onto compromised hosts for follow-on exploitation. Arctic Wolf...

Spotting insider threats can be more challenging for a simple reason: insiders already have legitimate access - whether limited or full - to an organization's network, systems, or other assets. "Identifying insider threats is not a binary process. Insiders can be malicious, lack the skills to do their jobs properly, or be victims of coercion. Thus, it is important to understand the different types of insider threats and the vectors that are most applicable to your organization," Mandiant researchers recently noted.

Hackers with links to the Kremlin are suspected to have infiltrated information technology company Hewlett Packard Enterprise's (HPE) cloud email environment to exfiltrate mailbox data. "The...

Automated Emulation is an open-source Terraform template designed to create a customizable, automated breach and attack simulation lab. The creator of Automated Emulation, Jason Ostrom, aimed to develop an infrastructure security lab to enhance skills in adversary simulation, focusing on linking TTPs and evaluating various endpoint security products.

In this Help Net Security interview, Nate Warfield, Director of Threat Research and Intelligence at Eclypsium, outlines the crucial tasks for CISOs in protecting supply chains and achieving comprehensive visibility. Auditing a hardware supply chain is exponentially more difficult, as vendors may or may not choose to disclose what their underlying operating systems are, what open source software they use, where they source the hardware components of their devices, what firmware runs both the device itself and its subcomponents - for example a router may run a Linux distribution, with an open source routing daemon, a motherboard from Supermicro, with high-speed NICs from Mellanox, a baseboard management controller from ASPEED with BMC code from AMI which itself is another version of Linux with its own SBOM. With the apparent disconnect between security and development teams in software supply chain security, what strategies do you recommend to enhance collaboration?

AI and ML deserve the hype they get, but the focus can't always be on the glitz. As these advances to deliver real benefits, there's a slew of more mundane actions that have to be taken-and in 2024, this is where we'll see some of the most exciting moves.

Blind spots and critical vulnerabilities are worsening, with 45% of critical CVEs remaining unpatched.The educational services industry has a significantly higher percentage of servers with unpatched weaponised Common Vulnerabilities and Exposures, compared to the general average of 10%. Industries still using end-of-life or EoS OSs that are no longer actively supported or patched for vulnerabilities and security issues by the manufacturer: Educational services, retail trade, healthcare, manufacturing and public administration.

HPE has become the latest tech giant to admit it has been compromised by Russian operatives. HPE "Immediately activated our response process to investigate, contain, and remediate the incident, eradicating the activity."

A US court has rejected spyware vendor NSO Group's motion to dismiss a lawsuit filed by Apple that alleges the developer violated computer fraud and other laws by infecting customers' iDevices with its surveillance software. Apple sued NSO, developer of the notorious Pegasus spyware, back in November 2021 and asked the court to permanently ban NSO from using any Apple software, services, or devices.