Security News > 2023 > October

A critical vulnerability tracked as CVE-2023-4966 in Citrix NetScaler ADC/Gateway devices has been actively exploited as a zero-day since late August, security researchers announced. A report from Mandiant disclosed that it found signs of CVE-2023-4966 being exploited in the wild since August for stealing authentication sessions and hijacking accounts.

Hackers are scanning for internet-exposed Jupyter Notebooks to breach servers and deploy a cocktail of malware consisting of a Linux rootkit, crypto miners, and password-stealing scripts. In a new campaign called 'Qubitstrike,' the threat actors download malicious payloads to hijack a Linux server for cryptomining and to steal credentials for cloud services, such as AWS and Google Cloud.

Twitter, now renamed X, is testing new $1 annual subscriptions to provide unverified accounts access to core features like tweeting and retweeting. Set up as a recurring subscription service, the program provides unverified Twitter accounts with what the company describes as "Write-level functionality."

The complexity and change experienced by organisations as they grow is one reason we are seeing similar cyber security risks to a decade ago, says Rapid7's CISO Jaya Baloo. Speaking on ethics in information security at the 2023 Australian Cyber Conference, Baloo said the Australian market has truly woken up to cyber risks in the last year due to a number of high-profile data breaches that have affected millions of Australians.

Government entities in the Asia-Pacific (APAC) region are the target of a long-running cyber espionage campaign dubbed TetrisPhantom. "The attacker covertly spied on and harvested sensitive data...

Cisco Talos discovered a new critical zero-day vulnerability in the Web User Interface feature of Cisco IOS XE software that's currently being used in the wild. The vulnerability used to access the system and create those accounts is CVE-2023-20198; it received the highest Common Vulnerability Scoring System score of 10.

Microsoft has disabled a bad anti-spam rule flooding Microsoft 365 admins' inboxes with blind carbon copies of outbound emails mistakenly flagged as spam. This false positive issue affected Exchange Online users worldwide, with many reports saying that all emails sent to external addresses were being tagged as spam.

The FBI warns that cybercriminals are using spoofed emails and phone numbers to target plastic surgery offices across the United States for extortion in phishing attacks that spread malware. "Cybercriminals use open-source information, to include social media, and social engineering techniques to enhance the harvested ePHI data of plastic surgery patients," the FBI said.
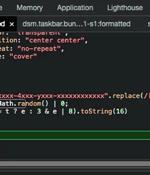
A medium-severity flaw has been discovered in Synology's DiskStation Manager (DSM) that could be exploited to decipher an administrator's password and remotely hijack the account. "Under some rare...

Cyber warfare and cyber attackers are an ever-present threat, as state-sponsored bad actors and individual cybercriminals alike continue to evolve their tactics. Due to the changing nature of cyber threats and attack methods, defense strategists often struggle to discern whether a cyberattack is classified as an "Armed attack" or an "Imminent armed attack." Unlike traditional military attacks, cyberattacks can originate from anywhere, and attackers often leverage sophisticated tactics to obscure the perpetrator's identity.