Security News > 2023 > August

Lax policies for package naming on Microsoft's PowerShell Gallery code repository allow threat actors to perform typosquatting attacks, spoof popular packages and potentially lay the ground for massive supply chain attacks. PowerShell Gallery is a Microsoft-run online repository of packages uploaded by the wider PowerShell community, hosting a large number of scripts and cmdlet modules for various purposes.

ATMs always take your card right in, don't they? So the idea of these ATM skimming crooks is they're not just interested in your card details, like a web phisher would be.

An ongoing phishing campaign has been underway since at least April 2023 that attempts to steal credentials for Zimbra Collaboration email servers worldwide. According to the ESET researchers, the attacks start with a phishing email pretending to be from an organization's admin informing users of an imminent email server update, which will result in temporary account deactivation.

Code development, content creation and analytics are the top generative AI use cases. A little over half of businesses have experimented with AI. Surveyed companies using generative AI employed it in content generation, analytics insights summary, analytics insights generation, code development and process documentation.

A very useful and previously unknown Windows tip was revealed this week, where you can halt process jumping in Task Manager by holding down the Ctrl key on your keyboard, allowing easier access to a listed process. The Windows Task Manager is one of the most useful built-in tools for managing your system, allowing you to terminate unresponsive applications and see what processes are using too much CPU, memory, and other resources.

A previously undetected attack method called NoFilter has been found to abuse the Windows Filtering Platform to achieve privilege escalation in the Windows operating system. "If an attacker has the ability to execute code with admin privilege and the target is to perform LSASS Shtinkering, these privileges are not enough," Ron Ben Yizhak, a security researcher at Deep Instinct, told The Hacker News.
An ongoing cyber attack campaign originating from China is targeting the Southeast Asian gambling sector to deploy Cobalt Strike beacons on compromised systems. "The threat actors abuse Adobe Creative Cloud, Microsoft Edge, and McAfee VirusScan executables vulnerable to DLL hijacking to deploy Cobalt Strike beacons," security researchers Aleksandar Milenkoski and Tom Hegel said in an analysis published today.

Threat actors increasingly distribute malicious Android APKs that resist decompilation using unsupported, unknown, or heavily tweaked compression algorithms. Zimperium, a member of the 'App Defense Alliance' dedicated to identifying and eliminating malware from Google Play, analyzed the decompilation resistance landscape after a Joe Security tweet that showcased an APK that eludes analysis yet runs seamlessly on Android devices.
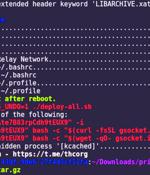
A new, financially motivated operation dubbed LABRAT has been observed weaponizing a now-patched critical flaw in GitLab as part of a cryptojacking and proxyjacking campaign. Proxyjacking allows the attacker to rent the compromised host out to a proxy network, making it possible to monetize the unused bandwidth.

Cybersecurity researchers have documented a novel post-exploit persistence technique on iOS 16 that could be abused to fly under the radar and main access to an Apple device even when the victim believes it is offline. The method "Tricks the victim into thinking their device's Airplane Mode works when in reality the attacker has planted an artificial Airplane Mode which edits the UI to display Airplane Mode icon and cuts internet connection to all apps except the attacker application," Jamf Threat Labs researchers Hu Ke and Nir Avraham said in a report shared with The Hacker News.