Security News > 2023 > July

The top focus areas for chief audit executives in 2023 are advancing data analytics, assuring proliferating digital risks, and talent management, according to Gartner. "In 2023 most CAEs are focusing on organizational and departmental digital transformation initiatives and improving team engagement and performance in response to growing assurance needs," said Leslee McKnight, VP in the Gartner Risk & Audit Practice.

The Cisco SD-WAN vManage management software is impacted by a flaw that allows an unauthenticated, remote attacker to gain read or limited write permissions to the configuration of the affected...

Exec faces fraud charges, one regulator wants $5 billion fine Alex Mashinsky, the now-former CEO of collapsed cryptocurrency concern Celsius, today faces charges of fraud as prosecutors and...

Google is fighting back against the constant invasion of malware on Google Play by requiring all new developer accounts registering as an organization to provide a valid D-U-N-S number before submitting apps. Typically, malicious apps on Google Play are submitted for review without dangerous code or payloads, which are then fetched later via an update in the post-installation phase.

Among the strategic propositions in Gartner's 2023-2024 cybersecurity outlook are that organizations need to institute cultural changes to lower pressure on security teams.

Microsoft announced today that the upcoming Windows 11, version 23H2, will be available in the fourth quarter of 2023 as an enablement package since it shares Windows 11 22H2's code base and servicing branch. The enablement package will act as a "Master switch" that will toggle on the inactive 23H2 features and upgrade the Windows version and build number.

DUCK. Yes, the usual large number of bugs fixed. Although Elevation of Privilege usually gets looked down on as lesser than Remote Code Execution, where crooks use the bug to break in in the first place, the problem with EoP has to do with crooks who are already "Loitering with intent" in your network.

Cybersecurity researchers and threat actors are targeted by a fake proof of concept CVE-2023-35829 exploit that installs a Linux password-stealing malware. The fake PoC claims to be an exploit for CVE-2023-35829, a high-severity use-after-free flaw impacting the Linux kernel before 6.3.2.

Zimbra urged admins today to manually fix a zero-day vulnerability actively exploited to target and compromise Zimbra Collaboration Suite email servers."A security vulnerability in Zimbra Collaboration Suite Version 8.8.15 that could potentially impact the confidentiality and integrity of your data has surfaced. [.] The fix is planned to be delivered in the July patch release," the company warned on Thursday via an advisory that doesn't inform customers the bug is also being abused in the wild.
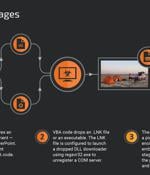
Government entities, military organizations, and civilian users in Ukraine and Poland have been targeted as part of a series of campaigns designed to steal sensitive data and gain persistent remote access to the infected systems. The intrusion set, which stretches from April 2022 to July 2023, leverages phishing lures and decoy documents to deploy a downloader malware called PicassoLoader, which acts as a conduit to launch Cobalt Strike Beacon and njRAT. "The attacks used a multistage infection chain initiated with malicious Microsoft Office documents, most commonly using Microsoft Excel and PowerPoint file formats," Cisco Talos researcher Vanja Svajcer said in a new report.