Security News > 2023 > April

Google's Threat Analysis Group has been monitoring and disrupting Russian state-backed cyberattacks targeting Ukraine's critical infrastructure in 2023. Google reports that from January to March 2023, Ukraine received roughly 60% of the phishing attacks originating from Russia, making it the most prominent target.

VMware addressed a critical vRealize Log Insight security vulnerability that allows remote attackers to gain remote execution on vulnerable appliances. The bug is described as a deserialization vulnerability that can be abused to run arbitrary code as root on compromised systems.

Threat groups are on the rise, and Google Cloud's cyberdefense unit Mandiant is tracking 3,500 of them, with 900 added last year, including 265 first identified during Mandiant's investigations in 2022. The study, based on Mandiant Consulting investigations of targeted attack activity between Jan. 1 and Dec. 31, 2022, found an increasing number of new malware families.

A new Lazarus campaign considered part of "Operation DreamJob" has been discovered targeting Linux users with malware for the first time. Lazarus' Operation DreamJob, also known as Nukesped, is an ongoing operation targeting people who work in software or DeFi platforms with fake job offers on LinkedIn or other social media and communication platforms.

Microsoft is investigating an ongoing outage blocking customers worldwide from accessing and using web apps and online services. The list of affected services includes Microsoft 365 fort the web, the Microsoft 365 suite, Microsoft Teams, and Microsoft Planner.
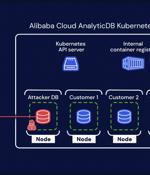
A chain of two critical flaws has been disclosed in Alibaba Cloud's ApsaraDB RDS for PostgreSQL and AnalyticDB for PostgreSQL that could be exploited to breach tenant isolation protections and access sensitive data belonging to other customers. "The vulnerabilities potentially allowed unauthorized access to Alibaba Cloud customers' PostgreSQL databases and the ability to perform a supply chain attack on both Alibaba database services, leading to an RCE on Alibaba database services," cloud security firm Wiz said in a new report shared with The Hacker News.

London-based professional outsourcing giant Capita has published an update on the cyber-incident that impacted it at the start of the month, now admitting that hackers exfiltrated data from its systems.On March 31, 2023, Capita disclosed an IT issue that impacted its services.

Business process outsourcing and tech services player Capita says there is proof that some customer data was scooped up by cyber baddies that broke into its systems late last month. "As a result of the interruption, the incident was significantly restricted, potentially affecting around 4 percent of Capita's server estate. There is currently some evidence of limited data exfiltration from the small proportion of affected server estate which might include customer, supplier or colleague data."

The supply-chain attack against 3CX last month was caused by an earlier supply-chain compromise of a different software firm - Trading Technologies - according to Mandiant, whose consulting crew was hired by 3CX to help the VoIP biz investigate the intrusion. "This is the first time that we've ever found concrete evidence of a software supply chain attack leading to another software supply chain attack," Mandiant Consulting CTO Charles Carmakal told reporters on Wednesday.

An investigation into last month's 3CX supply chain attack discovered that it was caused by another supply chain compromise where suspected North Korean attackers breached the site of stock trading automation company Trading Technologies to push trojanized software builds. According to Mandiant, the cybersecurity firm that helped 3CX investigate the incident, the threat group used harvested credentials to move laterally through 3CX's network, eventually breaching both the Windows and macOS build environments.