Security News > 2023 > March

Crown Resorts, Australia's largest gambling and entertainment company, has confirmed that it suffered a data breach after its GoAnywhere secure file-sharing server was breached using a zero-day vulnerability. This data breach was conducted by the Clop ransomware gang, which has shifted over the past year from encrypting files to performing data extortion attacks.

A fork bomb is a form of denial-of-service attack that uses the fork operation, which is executed recursively and can consume all system resources. How do you prevent this from happening? You lower the number of processes allowed on your Linux server.

Mandiant analysts who disclosed the activities of APT43 for the first time assess with high confidence that the threat actors are state-sponsored, aligning their operational goals with the North Korean government's geopolitical aims. The researchers have been tracking APT43 since late 2018 but have disclosed more specific details about the threat group only now.

Passwords can be insecure in other ways, such as reusing the same password across multiple sites, sharing a password with co-workers, or even remembering a password on a public computer. Avoid Password Sharing & Password Reuse - A unique password for each site and application, without sharing, ensures that a stolen password elsewhere won't compromise an organization.

Australian loan giant Latitude Financial Services is warning customers that its data breach is much more significant than initially stated, taking the number of affected individuals from 328,000 to 14 million. Australian loan giant Latitude Financial Services has released an updated data breach notification warning customers that the breach is much more significant than initially stated, taking the number of affected individuals from 328,000 to 14 million.
An advanced persistent threat group that has a track record of targeting India and Afghanistan has been linked to a new phishing campaign that delivers Action RAT. According to Cyble, which attributed the operation to SideCopy, the activity cluster is designed to target the Defence Research and Development Organization, the research and development wing of India's Ministry of Defence. Known for emulating the infection chains associated with SideWinder to deliver its own malware, SideCopy is a threat group of Pakistani origin that shares overlaps with Transparent Tribe.
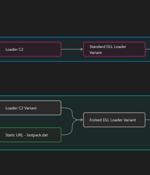
Multiple threat actors have been observed using two new variants of the IcedID malware in the wild with more limited functionality that removes functionality related to online banking fraud. "The well-known IcedID version consists of an initial loader which contacts a Loader server, downloads the standard DLL Loader, which then delivers the standard IcedID Bot," Proofpoint said in a new report published Monday.

Pen testing has become increasingly important as attackers have become more sophisticated and cybercrime has grown to include a variety of attack vectors. 32% of organizations do a pen test only once or twice a year because traditional pen testing methods have certain drawbacks that make it challenging to implement consistently for several reasons.

Apple has released security updates for - pardon the pop-culture reference - everyhing everywhere all at once, and has fixed the WebKit vulnerability exploited in the wild for users of older iPhones and iPads. The presently most important fix among those delivered is the one for CVE-2023-23529, a type confusion issue in the WebKit browser engine, which can be triggered by maliciously crafted web content and ultimately allow code execution.

Both Google’s Pixel’s Markup Tool and the Windows Snipping Tool have vulnerabilities that allow people to partially recover content that was edited out of images.