Security News > 2023 > February

Atlassian has confirmed that a breach at a third-party vendor caused a recent leak of company data and that their network and customer information is secure. As first reported by Cyberscoop, a hacking group known as SiegedSec leaked data on Telegram yesterday, claiming to be stolen from Atlassian, a collaboration software company based out of Australia.

Hackers are deploying a new malware named 'Frebniss' on Microsoft's Internet Information Services that stealthily executes commands sent via web requests. Microsoft IIS is a web server software that acts as a web server and a web app hosting platform for services like Outlook on the Web for Microsoft Exchange.

Chinese-speaking individuals in Southeast and East Asia are the targets of a new rogue Google Ads campaign that delivers remote access trojans such as FatalRAT to compromised machines. The attacks involve purchasing ad slots to appear in Google search results that direct users searching for popular applications to rogue websites hosting trojanized installers, ESET said in a report published today.
Security researchers have disclosed two new vulnerabilities affecting Schneider Electric Modicon programmable logic controllers that could allow for authentication bypass and remote code execution. The flaws, tracked as CVE-2022-45788 and CVE-2022-45789, are part of a broader collection of security defects tracked by Forescout as OT:ICEFALL. Successful exploitation of the bugs could enable an adversary to execute unauthorized code, denial-of-service, or disclosure of sensitive information.

According to internal Slack messages that were leaked to Insider, an Amazon lawyer told workers that they had "Already seen instances" of text generated by ChatGPT that "Closely" resembled internal company data. This issue seems to have come to a head recently because Amazon staffers and other tech workers throughout the industry have begun using ChatGPT as a "Coding assistant" of sorts to help them write or improve strings of code, the report notes.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.
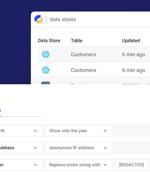
This is not the case when it comes to sensitive data sitting in production or analytic databases, data warehouses or data lakes. This article examines how Satori, a data security platform, gives control of the sensitive data in databases, data warehouses and data lakes to the security teams.

Telecommunication service providers in the Middle East are being targeted by a previously undocumented threat actor as part of a suspected espionage-related campaign. NET-based backdoors such as CMD365 or CMDEmber that leverage Microsoft 365 Mail and Google Firebase for C2. "The main functionality of CMD365 and CMDEmber is to execute attacker-provided system commands using the Windows command interpreter," the researchers said.
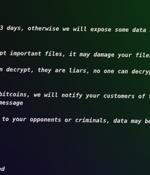
More than 500 hosts have been newly compromised en masse by the ESXiArgs ransomware strain, most of which are located in France, Germany, the Netherlands, the U.K., and Ukraine. Some of the crucial differences between the two ransom notes include the use of an onion URL instead of a Tox chat ID, a Proton Mail address at the bottom of the note, and a lower ransom demand.

Each year at the end of January, internet users are deluged with advice on how to keep their data protected and reclaim their online privacy. What started as Data Privacy Day has now become a Week, to match our increasing dependency on the internet and help us navigate treacherous online privacy waters.