Security News > 2022 > August

Google Workspace now has stronger protections for risky account actions, automatically blocking hijacking attempts with identity verification prompts and logging them for further investigation. The enhanced account protection capabilities are available to all Google Workspace customers, including legacy G Suite Basic and Business customers.

Simply finding vulnerabilities and patching them "Is totally useless," according to Google's Eduardo Vela, who heads the cloud giant's product security response team. Instead, they've got to exploit the bug: connect to Google Kubernetes Engine instances, hack it, and use the bug to steal the hidden flags.

Figure A. Dark Utilities provides code which needs to be executed on a target's system, which means the attacker needs to have already compromised the system and have access to it. The documentation provided by the platform provides guidance for conducting reconnaissance and identifying/exploiting vulnerabilities to infect servers that can be added to Dark Utilities.

An ongoing outage affects multiple Microsoft 365 services, blocking users from connecting to Exchange Online, Microsoft Teams, Outlook desktop clients, and OneDrive for Business. While Microsoft says that this incident has only affected customers in the EMEA region, users have been reporting server connection issues and sign-in failures worldwide.

Cloudflare says it was subject to a similar attack to one made on comms company Twilio last week, but in this case it was thwarted by hardware security keys that are required to access applications and services. According to Cloudflare, it recorded a very similar incident late last month, which could suggest the two attacks may have originated from the same attacker or group.

Microsoft is urging users to patch a zero-day vulnerability dubbed Dogwalk that is actively being exploited in the wild. The actively exploited Dogwalk bug was first reported to Microsoft in January 2020 by researcher Imre Rad. However, it wasn't until a separate researchers began tracking the exploitation of a flaw dubbed Follina that the Dogwalk bug was rediscovered.

Why? GitLab explained: "Due to Microsoft Windows' dominance in desktop operating systems, Windows is the platform most targeted by spyware, viruses, and ransomware." Windows' security mess has never been just because Windows is more popular.

For the most part, hackers don't even have to hide in the dark recesses of the web to take advantage of people any longer; they can be found right in plain sight on social media sites or forums, professionally advertised with their websites, and may even approach you anonymously through such channels as Twitter. A series of new DDoS for Hire are commoditizing the art of hacking and reducing the barrier to launching DDoS attacks.

Cybercriminals and threat actors work around the clock, with attacks originating from around the world. All businesses, including SMBs, need to be always on alert for new threats and available to respond at any moment to an incident.
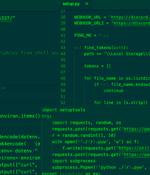
In what's yet another instance of malicious packages creeping into public code repositories, 10 modules have been removed from the Python Package Index for their ability to harvest critical data points such as passwords and Api tokens. The packages "Install info-stealers that enable attackers to steal developer's private data and personal credentials," Israeli cybersecurity firm Check Point said in a Monday report.