Security News > 2022 > July

Protect your business from cybercrime with this dark web monitoring service We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. In addition to using a VPN and anti-malware software, it's also smart to invest in a service like Dark Web Monitoring for Business.

Kubernetes security is essentially a collection of techniques, strategies, and technologies created to protect the Kubernetes platform and the containers it handles. Kubernetes security addresses three main concerns: the K8s API, best practices for pod container security, and the 4 C's of cloud-native security, namely container, cluster, code, and the cloud itself.

Kaspersky is reporting on a new UFEI rootkit that survives reinstalling the operating system and replacing the hard drive. The firmware compromises the UEFI, the low-level and highly opaque chain of firmware required to boot up nearly every modern computer.

MSSPs must find ways to balance the need to please existing customers, add new ones, and deliver high-margin services against their internal budget constraints and the need to maintain high employee morale. This means providing the right tool sets, driving higher efficiency through training, and scaling services to build revenue and margin.

The rise of DevOps culture in enterprises has accelerated product delivery timelines. Automation undoubtedly has its advantages. However, containerization and the rise of cloud software...
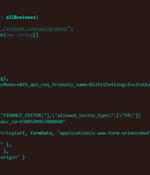
Facebook business and advertising accounts are at the receiving end of an ongoing campaign dubbed Ducktail designed to seize control as part of a financially driven cybercriminal operation. "The malware is designed to steal browser cookies and take advantage of authenticated Facebook sessions to steal information from the victim's Facebook account and ultimately hijack any Facebook Business account that the victim has sufficient access to."

Google has brought its Street View service - which offers photographs of most locations on Google Maps - back to India, six years after the nation rejected it as an invasion of privacy and a threat to national security. India blocked Street View in 2016 due to national security authorities feeling that freely available photography could assist terrorists.

How attackers are adapting to a post-macro world We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. After Microsoft announced it would begin blocking VBA and XL4 macros by default for Windows Office applications late last year, attackers began using container files such as ISO and RAR attachments and Windows shortcut files to deliver payloads instead. "We are seeing behaviors shift across the entire threat landscape, and as our researchers mention in the report, they assess with high confidence this is one of the largest email threat landscape shifts in recent history," said Sherrod DeGrippo, vice president of Threat Research and Detection at Proofpoint.

Hackers who normally distributed malware via phishing attachments with malicious macros gradually changed tactics after Microsoft Office began blocking them by default, switching to new file types such as ISO, RAR, and Windows Shortcut attachments.VBA and XL4 Macros are small programs created to automate repetitive tasks in Microsoft Office applications, which threat actors abuse for loading, dropping, or installing malware via malicious Microsoft Office document attachments sent in phishing emails.

Increased cyber threats and government directives have made cybersecurity a top priority among critical infrastructure organizations. This Help Net Security video highlights how leaders rethink their approach to cybersecurity for operations.