Security News > 2022 > June

Overall, the survey finds that strong passwords remain a priority strategy and are important in shoring up the confidence of enterprise security decision makers. Weak passwords are vulnerable to password theft or compromise, which has led the enterprise to complement passwords with strategies such as OTP, email verification codes, SMS, or biometric factors.
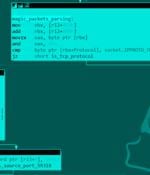
A new covert Linux kernel rootkit named Syslogk has been spotted under development in the wild and cloaking a malicious payload that can be remotely commandeered by an adversary using a magic network traffic packet. "The Syslogk rootkit is heavily based on Adore-Ng but incorporates new functionalities making the user-mode application and the kernel rootkit hard to detect," Avast security researchers David Álvarez and Jan Neduchal said in a report published Monday.
As many as eight zero-day vulnerabilities have been disclosed in Carrier's LenelS2 HID Mercury access control system that's used widely in healthcare, education, transportation, and government facilities. "The vulnerabilities uncovered allowed us to demonstrate the ability to remotely unlock and lock doors, subvert alarms and undermine logging and notification systems," Trellix security researchers Steve Povolny and Sam Quinn said in a report shared with The Hacker News.
Cybersecurity researchers have detailed the workings of a fully-featured malware loader dubbed PureCrypter that's being purchased by cyber criminals to deliver remote access trojans and information stealers. Some of the malware families distributed using PureCrypter include Agent Tesla, Arkei, AsyncRAT, AZORult, DarkCrystal RAT, LokiBot, NanoCore, RedLine Stealer, Remcos, Snake Keylogger, and Warzone RAT. Sold for a price of $59 by its developer named "PureCoder" for a one-month plan since at least March 2021, PureCrypter is advertised as the "Only crypter in the market that uses offline and online delivery technique."

It leverages "Speculative execution attacks to bypass an important memory protection mechanism, ARM Pointer Authentication, a security feature that is used to enforce pointer integrity," MIT researchers Joseph Ravichandran, Weon Taek Na, Jay Lang, and Mengjia Yan said in a new paper. The vulnerability is rooted in pointer authentication codes, a line of defense introduced in arm64e architecture that aims to detect and secure against unexpected changes to pointers - objects that store a memory address - in memory.

Cybersecurity researchers have disclosed details of two medium-security flaws in Mitel 6800/6900 desk phones that, if successfully exploited, could allow an attacker to gain root privileges on the devices. Tracked as CVE-2022-29854 and CVE-2022-29855, the access control issues were discovered by German penetration testing firm SySS, following which patches were shipped in May 2022.

Kaiser Permanente, one of America's leading not-for-profit health plans and health care providers, has recently disclosed a data breach that exposed the health information of more than 69,000 individuals. Founded in 1945, Kaiser Permanente provides health care services to over 12.5 million members from 8 U.S. states and Washington, D.C. The company revealed in a notice published on its website that an attacker accessed an employee's email account containing patients' protected health information on April 5, 2022, without authorization.

The Gallium state-sponsored hacking group has been spotted using a new 'PingPull' remote access trojan against financial institutions and government entities in Europe, Southeast Asia, and Africa. Gallium is believed to originate from China, and its targeting scope of the telecommunications, finance, and government sectors in espionage operations aligns with the country's interests.

This retirement affects Internet Explorer 11 desktop apps on specific versions of Windows 10 delivered via the Semi-Annual Channel to systems running Windows 10 client SKUs and Windows 10 IoT. Internet Explorer is also not available on Windows 11, where the new Chromium-based Microsoft Edge is the default web browser. Windows releases where Internet Explorer will still be available after June 15, 2022, include Windows 7 ESU, Windows 8.1, and all versions of Windows 10 LTSC client, IoT, and Server.

In a recent report, Confiant notes that the malicious cryptocurrency apps are identical to the real ones but they come with a backdoor that can steal the users' security phrase for accessing the digital assets. Confiant analysts reversed engineer the apps to figure out how SeaFlower authors had planted the backdoors and found similar code in all of them.