Security News > 2022 > April

A server-side request forgery flaw in an API of a large financial technology platform potentially could have compromised millions of bank customers, allowing attackers to defraud clients by controlling their bank accounts and funds, researchers have found. A team at Salt Security's Salt Labs identified the vulnerability in an API in a web page that supports the organization's platform fund transfer functionality, which allows clients to transfer money from their accounts on its platform into their bank accounts, researchers disclosed in a report published Thursday.

Malicious Android apps found masquerading as legitimate antivirus tools. In a report released Thursday, the cyber threat intelligence provider detailed its discovery of six apps in Google Play that appeared to be antivirus software but actually tried to install malware capable of stealing credentials and financial data.

The Threat Hunter Team team is attributing the attacks to Cicada, also known as APT10 - a group that has been operating for more than a decade and that intelligence agencies in the US have linked to China's Ministry of State Security. The researchers are pointing at Cicada because a custom loader and custom malware that have been used exclusively by the group were found in victims' networks.

"The operation copied and removed malware from vulnerable internet-connected firewall devices that Sandworm used for command and control of the underlying botnet. Although the operation did not involve access to the Sandworm malware on the thousands of underlying victim devices worldwide, referred to as 'bots,' the disabling of the C2 mechanism severed those bots from the Sandworm C2 devices' control," the US DOJ stated. The malware targeted networking devices by WatchGuard and ASUS. "These network devices are often located on the perimeter of a victim's computer network, thereby providing Sandworm with the potential ability to conduct malicious activities against all computers within those networks," the DOJ stated.

An XM Cyber report reveals the security gaps and hygiene issues that exist in multiple attack paths across on-prem and cloud environments, demonstrating the importance of risk visibility across the entire network. Organizations today are increasingly investing in new technology to boost their business, but don't realize that, since these technologies are all connected, they pose a great risk to critical assets.

As in the Coinbase incident, many MFA bypass attacks begin with a phishing attack. Organizations use MFA to protect users against these attacks.

Cado Security says it has discovered a strain of malware specifically designed to run in AWS Lambda serverless environments and mine cryptocurrency. While the security firm has only seen the malware running in AWS Lambda, it can be made to run in other Linux-flavored environments, Cado Security CTO and co-founder Chris Doman told The Register this week.
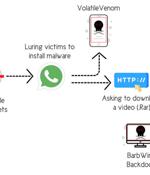
A threat actor with affiliations to the cyber warfare division of Hamas has been linked to an "Elaborate campaign" targeting high-profile Israeli individuals employed in sensitive defense, law enforcement, and emergency services organizations. "The campaign operators use sophisticated social engineering techniques, ultimately aimed to deliver previously undocumented backdoors for Windows and Android devices," cybersecurity company Cybereason said in a Wednesday report.
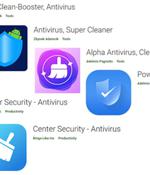
As many as seven malicious Android apps discovered on the Google Play Store masqueraded as antivirus solutions to deploy a banking trojan called SharkBot. "SharkBot steals credentials and banking information," Check Point researchers Alex Shamshur and Raman Ladutska said in a report shared with The Hacker News.

In this video for Help Net Security, Tal Samra, Cyber Threat Analyst at Cyberint, talks about Discord, a platform often used for cybercrime activities, and the possible threats users might come across. The application offers its users privacy and encryption, access to private rooms and hidden content, and by also being resistant to law enforcement seizure, it has been increasingly leveraged by cybercriminals in distributing malicious files.