Security News > 2022 > January
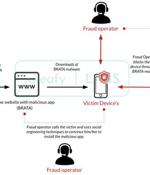
The Android malware tracked as BRATA has been updated with new features that grants it the ability to track device locations and even perform a factory reset in an apparent bid to cover up fraudulent wire transfers. "What makes Android RAT so interesting for attackers is its capability to operate directly on the victim devices instead of using a new device," Cleafy researchers noted in December 2021.

A massive Minecraft tournament styled after the Netflix blockbuster Squid Game apparently inspired a distributed denial of service attack that took down the sole internet service provider in Andorra. Confirmed: Internet disruption registered on #Andorra Telecom on Saturday evening; the incident is attributed by the state telco to a DDoS attack targeting the high-stakes #SquidCraftGames Minecraft Twitch competition, resulting in the elimination of Team Andorra pic.

Ozzy Osbourne and his famously enterprising wife and manager Sharon decided to launch a new non-fungible token collection called CryptoBatz, but the rollout was clouded by scammers who used an abandoned vanity Discord URL to drain users' crypto wallets out of at least $150,000 worth of Ethereum. A tweak to the CryptoBatz vanity URL by the company behind the project, Sutter Systems, mistakenly left the old URL active, along with old tweets referencing the abandoned URL. Soon scammers set up a dummy Discord server with the old URL and started targeting users and draining their crypto wallets, according to Malwarebytes Labs.

A vulnerability in Polkit's pkexec component identified as CVE-2021-4034 is present in the default configuration of all major Linux distributions and can be exploited to gain full root privileges on the system, researchers warn today. Researchers at Qualys information security company found that the pkexec program could be used by local attackers to increase privileges to root on default installations of Ubuntu, Debian, Fedora, and CentOS. They warn that PwnKit is likely exploitable on other Linux operating systems as well.

A vulnerability in Polkit's pkexec component that is present in the default configuration of all major Linux distributions can be exploited to gain full root privileges on the system, researchers warn today. Identified as CVE-2021-4034 and named PwnKit, the security issue has been tracked to the initial commit of pkexec, more than 12 years ago, meaning that all Polkit versions are affected.
Segway, maker of the iconic - and much-spoofed - personal motorized transporter familiar from guided city tours everywhere, has been serving up a nasty credit-card harvesting skimmer via its website - likely linked to Magecart Group 12. Magecart is a loose umbrella term encompassing various affiliated groups of financially motivated cybercriminals who all employ a similar skimming malware to harvest information - in particular payment-card information - that shoppers enter into checkout pages on eCommerce websites.

The notorious TrickBot malware has received new features that make it more challenging to research, analyze, and detect in the latest variants, including crashing browser tabs when it detects beautified scripts. TrickBot has dominated the malware threat landscape since 2016, constantly adding optimizations and improvements while facilitating the deployment of damaging malware and ransomware strains.

In South Africa, you get an IRP5 at the end of the tax year - an archaic term that we are guessing is short for Inland Revenue/Personal, Form #5, even though the South African tax office hasn't been called the Inland Revenue for nearly 25 years. Here at Naked Security, we know the names of these forms, amongst numerous others, because they often show up in tax scam emails, presumably to give those messages an air of realism.

A new family of cyber-espionage malware targeting macOS and delivered via a Safari exploit was used against politically active, pro-democracy residents of Hong Kong, in August watering-hole attacks initially discovered by Google TAG, researchers said on Tuesday. The watering-hole attacks - which TAG reported to Apple that same month - were serving an in-the-wild malware that exploited what was then a zero-day flaw to install a backdoor on the iOS and macOS devices of users who visited Hong Kong-based media and pro-democracy sites.

The United Kingdom's National Cyber Security Centre, the government agency that leads UK's cyber security mission, is releasing NMAP Scripting Engine scripts to help defenders scan for and remediate vulnerable systems on their networks. The scripts, authored by i100 partners or security experts who want to share their scripts with the community, will be published on GitHub through a new project named Scanning Made Easy.