Security News > 2021 > November

The transformation of the global workforce accelerated in 2021, driven by the continued impact of the pandemic and strains on businesses amid record labor shortages and shifting worker priorities. "The world of work has been in a constant state of motion," said Don Weinstein, corporate VP of global product and technology at ADP. "The needs of the global workforce are evolving in tandem with technology, and the result is transformational. Amid all the change, one common thread has only grown stronger: people power performance."
68% of Americans admitted to using the same password on multiple accounts and 64% only change their passwords if they have to, leaving them vulnerable to cybercrime. "What consumers aren't considering is that these behaviors make them vulnerable to digital crime when people outside your household - even ones you trust - have your passwords on their devices."

The research finds that investments in automation are directly linked to increased business revenues, job growth, and long-term productivity. Automation investments boost revenue and economic resilience.
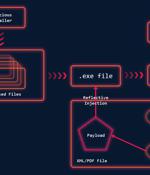
A new malware campaign has been discovered targeting cryptocurrency, non-fungible token, and DeFi aficionados through Discord channels to deploy a crypter named "Babadeda" that's capable of bypassing antivirus solutions and stage a variety of attacks. "[T]his malware installer has been used in a variety of recent campaigns to deliver information stealers, RATs, and even LockBit ransomware," Morphisec researchers said in a report published this week.

Researchers have unearthed a new remote access trojan for Linux that employs a never-before-seen stealth technique that involves masking its malicious actions by scheduling them for execution on February 31st, a non-existent calendar day. Dubbed CronRAT, the sneaky malware "Enables server-side Magecart data theft which bypasses browser-based security solutions," Sansec Threat Research said.
![S3 Ep60: Exchange exploit, GoDaddy breach and cookies made public [Podcast]](/static/build/img/news/s3-ep60-exchange-exploit-godaddy-breach-and-cookies-made-public-podcast-small.jpg)
" Cybersecurity tips for the holiday season and beyond. Tech history: What do you mean, "It uses a mouse?" Don't make your cookies public! Oh! No! DDoS attack in progress - unfurl the umbrellas!

A UK Department for Transport website was caught serving porn earlier today. Uk website was seen serving porn today, as confirmed by BleepingComputer.

Black Friday is approaching, and cybercriminals are honing their malware droppers, phishing lures, and fake sites while shoppers prepare to open their wallets. The security firm shared a detailed report highlighting the most common threats expected to surface during this year's Black Friday, as well as the Christmas shopping season.

A sad-faced Microsoft engineer has had to reset the "Days since we last shot ourselves in the foot" counter at the company's HQ after a security update broke Microsoft Defender for Endpoint on Windows Server Core. The latter included the LTSC editions of Windows 10 as Microsoft pointed out, only devices with a Windows Server Core installation were affected.

This holds true as attackers become more organised - constantly tweaking threat vectors, studying widely-used security playbooks, or testing their attacks against ancient security tools like IDPS. By relying on signatures to detect known threats and following the same old approaches, you're always going to be caught out by modern attackers, who already have the tools to bypass these dated defenses. I still see 90% of CISOs today are "Playing it safe", clinging to old playbooks and legacy tools like IDPS. Perhaps it ticks a box for them by filling a control gap, or maybe the board is tired of security asking for new products, or these tools are just seen as "Tried and tested." The inconvenient truth is that we can't sit on our laurels in security, or we'll be completely exposed to attacks like Sunburst and Colonial Pipeline.