Security News > 2021 > September

Cybercriminals are using Telegram bots to steal one-time password tokens and defraud people through banks and online payment systems, including PayPal, Apple Pay and Google Pay, new research has found. Threat actors are using Telegram bots and channels and a range of tactics to gain account information, including calling victims, and impersonating banks and legitimate services, researchers said.

Password managers are a good way to keep your passwords unique, strong and safe. A password manager is still the best way that balances convenience and security-with a heavy tilt toward security.
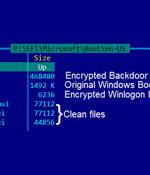
Commercially developed FinFisher surveillanceware has been upgraded to infect Windows devices using a UEFI bootkit using a trojanized Windows Boot Manager, marking a shift in infection vectors that allow it to elude discovery and analysis. While the tool was previously deployed through tampered installers of legitimate applications such as TeamViewer, VLC, and WinRAR that were backdoored with an obfuscated downloader, subsequent updates in 2014 enabled infections via Master Boot Record bootkits with the goal of injecting a malicious loader in a manner that's engineered to slip past security tools.

As the UK infosec industry prepares for government initiatives intended to expand the sector, how should existing companies keep skilled professionals from jumping ship? Amanda Finch, CEO of the Chartered Institute of Information Security, tells us a thing or two about what she thinks works. "People tend to stay in roles if they are being developed," Finch tells The Register just after the institute's annual conference.

Security intelligence vendor Flashpoint claims to have found forum comments from customers of the REvil ransomware-as-a-service gang, and they're not happy. The gang's malware may contain backdoors that REvil uses to restore encrypted files itself.

A second major reason is that ransomware attacks tend to attack two areas of the infrastructure that have traditionally been ignored - namely applications and data stored in files. Finding a next-generation data protection solution that utilizes a network approach, but at the data level, companies can protect what is typically most vulnerable.

You are the co-author of the Official² CISSP CBK Reference, now in it's 6th edition. There's a LOT that goes into writing a book - especially a technical reference.
![[eBook] Your First 90 Days as CISO — 9 Steps to Success](/static/build/img/news/ebook-your-first-90-days-as-ciso-9-steps-to-success-small.jpg)
The first 90 days for a new CISO are crucial in setting up their security team, so there is little time to waste, and much to accomplish. A new guide by XDR provider Cynet looks to give new and veteran CISOs a durable foundation to build a successful security organization.

Two newly discovered malicious Android applications on Google Play Store have been used to target users of Brazil's instant payment ecosystem in a likely attempt to lure victims into fraudulently transferring their entire account balances into another bank account under cybercriminals' control. "The attackers distributed two different variants of banking malware, named PixStealer and MalRhino, through two separate malicious applications [] to carry out their attacks," Check Point Research said in an analysis shared with The Hacker News.

In this interview with Help Net Security, Brandon Hoffman, CISO at Intel 471, talks about the growing threat of supply chain attacks, the most common supply chain vulnerabilities and how the right threat intelligence can help stay on top of these threats. We are witnessing a growing number of supply chain attacks lately, and cybercriminals are becoming stealthier and smarter.