Security News

PLUS: China spring cleans its AIs; South Korea fines Meta, probes Broadcom; and more! PLUS: China spring cleans its AIs; South Korea fines Meta, probes Broadcom; and more! India’s ambition to...

Zoho Vault is a business-focused password manager that provides convenient monitoring tools for administrators in large organizations. Figure D. While the password manager itself will work as advertised, I highly recommend also downloading Zoho Vault's browser extension.

Zoho Vault is a business-oriented password manager that shines in its security dashboards and reporting capabilities, which are perfect for larger organizations. Aside from password generation and storage, Zoho Vault comes with team-focused features that business managers will find useful.

The U.S. Cybersecurity and Infrastructure Security Agency on Thursday warned that multiple nation-state actors are exploiting security flaws in Fortinet FortiOS SSL-VPN and Zoho ManageEngine ServiceDesk Plus to gain unauthorized access and establish persistence on compromised systems. "Nation-state advanced persistent threat actors exploited CVE-2022-47966 to gain unauthorized access to a public-facing application, establish persistence, and move laterally through the network," according to a joint alert published by the agency, alongside Federal Bureau of Investigation, and Cyber National Mission Force.

State-backed hacking groups have breached a U.S. aeronautical organization using exploits targeting critical Zoho and Fortinet vulnerabilities, a joint advisory published by CISA, the FBI, and the United States Cyber Command revealed on Thursday. CISA was part of the incident response between February and April and said the hacking groups had been in the compromised aviation organization's network since at least January after hacking an Internet-exposed server running Zoho ManageEngine ServiceDesk Plus and a Fortinet firewall.
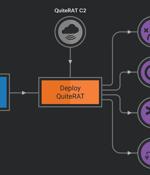
The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT. Targets include internet backbone infrastructure and healthcare entities in Europe and the U.S., cybersecurity company Cisco Talos said in a two-part analysis published today. What's more, a closer examination of the adversary's recycled attack infrastructure in its cyber assaults on enterprises has led to the discovery of a new threat dubbed CollectionRAT. The fact that the Lazarus Group continues to rely on the same tradecraft despite those components being well-documented over the years underscores the threat actor's confidence in their operations, Talos pointed out.

Multiple threat actors have been observed opportunistically weaponizing a now-patched critical security vulnerability impacting several Zoho ManageEngine products since January 20, 2023. Tracked as CVE-2022-47966, the remote code execution flaw allows a complete takeover of the susceptible systems by unauthenticated attackers.
Users of Zoho ManageEngine are being urged to patch their instances against a critical security vulnerability ahead of the release of a proof-of-concept exploit code. "This vulnerability allows an unauthenticated adversary to execute arbitrary code," Zoho warned in an advisory issued late last year, noting that it affects all ManageEngine setups that have the SAML single sign-on feature enabled, or had it enabled in the past.

On Friday, security researchers with Horizon3's Attack Team warned admins that they created a proof-of-concept exploit for CVE-2022-47966."The vulnerability is easy to exploit and a good candidate for attackers to 'spray and pray' across the Internet. This vulnerability allows for remote code execution as NT AUTHORITYSYSTEM, essentially giving an attacker complete control over the system," Horizon3 vulnerability researcher James Horseman said.

The U.S. Federal Bureau of Investigation and the Cybersecurity and Infrastructure Security Agency are warning of active exploitation of a newly patched flaw in Zoho's ManageEngine ServiceDesk Plus product to deploy web shells and carry out an array of malicious activities.Tracked as CVE-2021-44077, the issue relates to an unauthenticated, remote code execution vulnerability affecting ServiceDesk Plus versions up to, and including, 11305 that if left unfixed "Allows an attacker to upload executable files and place web shells that enable post-exploitation activities, such as compromising administrator credentials, conducting lateral movement, and exfiltrating registry hives and Active Directory files," CISA said.