Security News

Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Microsoft fixes actively exploited Windows CLFS zero-day (CVE-2025-29824) April 2025 Patch Tuesday...

WinRAR users, upgrade your software as soon as possible: a vulnerability (CVE-2025-31334) that could allow attackers to bypass Windows’ Mark of the Web (MotW) security warning and execute...

A vulnerability in the WinRAR file archiver solution could be exploited to bypass the Mark of the Web (MotW) security warning and execute arbitrary code on a Windows machine. [...]

WinRAR 7.10 was released yesterday with numerous features, such as larger memory pages, a dark mode, and the ability to fine-tune how Windows Mark-of-the-Web flags are propagated when extracting...

WinRAR 7.10 was released yesterday with numerous features, such as larger memory pages, a dark mode, and the ability to fine-tune how Windows Mark-of-the-Web flags are propagated when extracting...
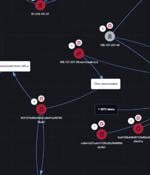
A hacktivist group known as Head Mare has been linked to cyber attacks that exclusively target organizations located in Russia and Belarus. "Head Mare uses more up-to-date methods for obtaining...
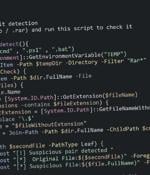
Cloudflare on Thursday said it took steps to disrupt a month-long phishing campaign orchestrated by a Russia-aligned threat actor called FlyingYeti targeting Ukraine. "The FlyingYeti campaign...

The threat actor known as UAC-0099 has been linked to continued attacks aimed at Ukraine, some of which leverage a high-severity flaw in the WinRAR software to deliver a malware strain called...

NDSC says that the Russian hackers used a Ngrok free static domain to access the command and control server hosted on their Ngrok instance. A report from Google in October notes that the security issue was exploited by Russian and Chinese state hackers to steal credentials and other sensitive data, as well as to establish persistence on target systems.

A hacking group that leveraged a recently disclosed security flaw in the WinRAR software as a zero-day has now been categorized as an entirely new advanced persistent threat (APT). Cybersecurity...