Security News

Even though your company may not have suffered a direct breach, your data may already be on the Dark Web. Breaches end up being marketed by hackers with data descriptions and auction demands, often in Bitcoin.

The guide, "Protection from web-borne threats starts with Browser Security Platform," details the characteristics and the capabilities of a potential solution, and explains how it compares to other security solutions and why it is needed. The guide calls for the recognition of an emerging security solution category, Browser Security Platform, which provides visibility into the browser's application layer.

Multiple criminals, including at least potentially one nation-state group, broke into a US federal government agency's Microsoft Internet Information Services web server by exploiting a critical three-year-old Telerik bug to achieve remote code execution. "Analysts determined that multiple cyber threat actors, including an APT actor, were able to exploit a.NET deserialization vulnerability in Progress Telerik user interface for ASP.NET AJAX, located in the agency's Microsoft Internet Information Services web server," the joint advisory said.

To get started on your training, we suggest checking out the Premium Ethical Hacking Certification Bundle, currently on sale for a limited time. It features eight courses that illustrate the basics of cyber security, shows students how to test various types of infrastructure and acquaints them with a lot of the tools that IT professionals use every day.

Reddit is investigating a major outage that is blocking users worldwide from accessing the social network's website and mobile apps. According to its official status page, Reddit confirmed that its website and apps are currently down, and its engineers looking into the root cause of this outage.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.
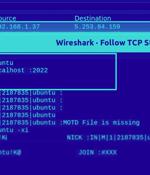
A new Golang-based malware dubbed GoBruteforcer has been found targeting web servers running phpMyAdmin, MySQL, FTP, and Postgres to corral the devices into a botnet. The malware is mainly designed to single out Unix-like platforms running x86, x64 and ARM architectures, with GoBruteforcer attempting to obtain access via a brute-force attack using a list of credentials hard-coded into the binary.

Secondly, introducing the dark web report in the U.S. will aid in better monitoring personal information.Google One has announced that VPN access will be expanded to all its plans, including the Basic plan that starts at $1.99/month.

Cisco has addressed a critical security vulnerability found in the Web UI of multiple IP Phone models that unauthenticated and remote attackers can exploit in remote code execution attacks. The security vulnerabilities were discovered by Zack Sanchez of the Cisco Advanced Security Initiatives Group during internal security testing.

The U.S. Cybersecurity and Infrastructure Security Agency has added a high-severity flaw affecting the ZK Framework to its Known Exploited Vulnerabilities catalog based on evidence of active exploitation. Tracked as CVE-2022-36537, the issue impacts ZK Framework versions 9.6.1, 9.6.0.1, 9.5.1.3, 9.0.1.2, and 8.6.4.1, and allows threat actors to retrieve sensitive information via specially crafted requests.