Security News

Abstract: The Common Vulnerability Scoring System is a popular method for evaluating the severity of vulnerabilities in vulnerability management. The goal of CVSS is to provide comparable scores across different evaluators.
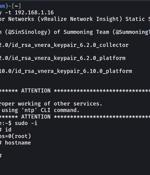
Proof-of-concept exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks. "A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to gain access to the Aria Operations for Networks CLI," VMware said earlier this week.

Proof-of-concept exploit code has been released for a critical SSH authentication bypass vulnerability in VMware's Aria Operations for Networks analysis tool.Today, VMware confirmed that CVE-2023-34039 exploit code has been published online, two days after disclosing the critical security bug.

VMware has patched one critical and one high-severity vulnerability in Aria Operations for Networks, its popular enterprise network monitoring tool. It could allow an attacker with network access to Aria Operations for Networks to bypass SSH authentication to gain access to the Aria Operations for Networks command-line interface.

VMware has released software updates to correct two security vulnerabilities in Aria Operations for Networks that could be potentially exploited to bypass authentication and gain remote code execution."A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to gain access to the Aria Operations for Networks CLI," the company said in an advisory.

A vulnerability in Skype mobile apps can be exploited by attackers to discover a user's IP address - a piece of information that may endanger individuals whose physical security depends on their general location remaining secret. Vulnerability specifics have not been publicly shared since it has yet to be patched, but Cox says it's "Trivially easy to exploit and involves changing a certain parameter related to the link."

Unpatched Citrix NetScaler systems exposed to the internet are being targeted by unknown threat actors in what's suspected to be a ransomware attack. Attack chains involve the exploitation of CVE-2023-3519, a critical code injection vulnerability impacting NetScaler ADC and Gateway servers that could facilitate unauthenticated remote code execution.

North Korean state-sponsored hackers Lazarus Group have been exploiting a ManageEngine ServiceDesk vulnerability to target internet backbone infrastructure and healthcare institutions in Europe and the US. The group leveraged the vulnerability to deploy QuiteRAT, downloaded from an IP address previously associated with the Lazarus hacking group. The malware Cisco Talos researchers dubbed QuiteRAT is a simple remote access trojan that's similar to Lazarus Group's MagicRAT malware, only smaller in size.

Ivanti is urging administrators of Ivanti Sentry gateways to patch a newly discovered vulnerability that could be exploited to change configuration, run system commands, or write files onto the vulnerable system. CVE-2023-38035 is an API authentication bypass flaw that may enable unauthenticated attackers to access APIs that are used to configure the Ivanti Sentry on the administrator portal/interface, which runs by default on port 8443.

The U.S. Cybersecurity and Infrastructure Security Agency has added a critical security flaw in Adobe ColdFusion to its Known Exploited Vulnerabilities catalog, based on evidence of active exploitation. The vulnerability, cataloged as CVE-2023-26359, relates to a deserialization flaw present in Adobe ColdFusion 2018 and ColdFusion 2021 that could result in arbitrary code execution in the context of the current user without requiring any interaction.